How to remove Yashma ransomware

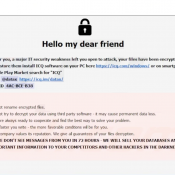
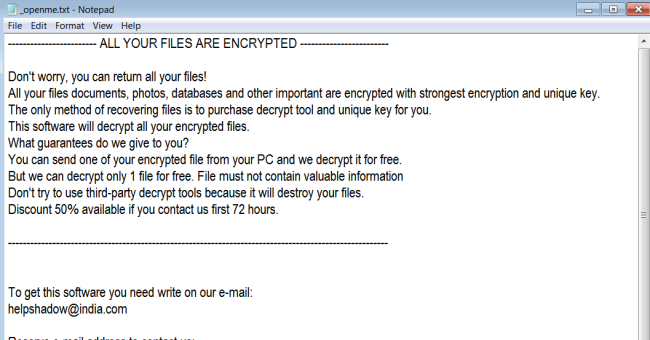
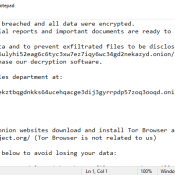
Yashma is a ransomware program derived from Chaos Ransomware. Generally speaking, ransomware refers to a category of malicious programs that exist to make money for a hacker by holding the victim’s files hostage. This is accomplished by first encrypting the files, rendering them inaccessible. Then, a ransom note is created, typically on the desktop, telling the victim that it is possible to decrypt the files by paying the hacker (usually in Bitcoin or another cryptocurrency).
However, Chaos ransomware is particularly malicious. Some variants of Chaos do not even bother actually decrypting the files, they just replace them with files consisting of random characters to pretend that they’re “encrypted”. Obviously, it is not possible to decrypt these files, though there’s still a chance they can be recovered by other means.
There are several reasons why you shouldn’t engage with the hackers. First, the payment they demand is very steep. Second, you have no guarantee that they’ll decrypt your files after you pay, and in some cases, it may not even be possible. Third, by paying the hackers you’re encouraging them to carry out further attacks.
The obvious alternative is to use anti-malware and anti-ransomware applications to remove Yashma ransomware yourself and, hopefully, restore the files. This guide will walk you through the process.