How to remove Re-captha-version-3-16.live
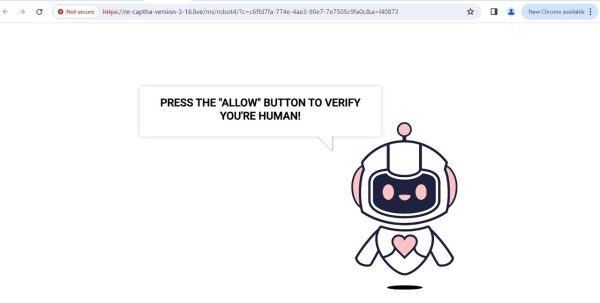
Re-captha-version-3-16.live is identified as a malicious website that engages in aggressive push notification spam and browser hijacking activities. It tricks users into enabling push notifications under false pretenses, such as verifying age or confirming that the user is not a robot. Once permission is granted, it bombards the user with intrusive spam advertisements, even when the browser is closed. This site operates by exploiting several tactics to infect users and propagate unwanted content, including compromised advertising networks, malvertising campaigns, social engineering tricks, software bundling, spam emails, and affiliate networks. The primary objective of Re-captha-version-3-16.live is to alter browser settings without the user's consent, leading to unwanted changes in the default search engine, homepage, and new tab settings. These modifications can redirect users to questionable websites, display excessive advertisements, and potentially expose them to phishing or other online threats. It is considered a potentially unwanted software that can compromise the security of a system. To remove Re-captha-version-3-16.live and its effects, users are advised to follow specific removal guides that involve checking browser extensions, altering browser settings, and using malware removal tools. It's also recommended to block browser notifications and use ad-blocking extensions like AdGuard to prevent similar attacks in the future.