How to remove TeslaCrypt ransomware
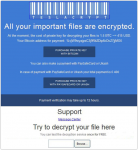
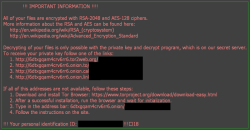
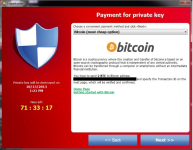
Teslacrypt is a ransomware application that was released in February 2015. The ransomware is designed to infect all versions of Windows existing at the moment. Settled on a victim’s system TeslaCrypt makes changes on a system level, which start with disabling of Windows Task Manager, Regedit and Command Prompt tools. Blocking of these utilities is aimed to complicate the removal process and to tighten the pressure showing the user that the computer is totally under the control of the ransomware.