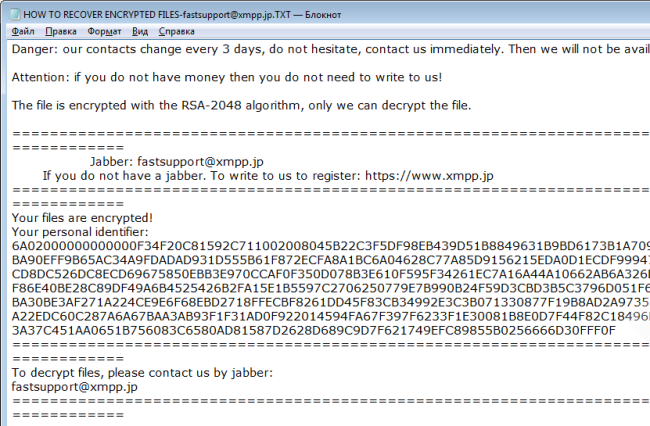
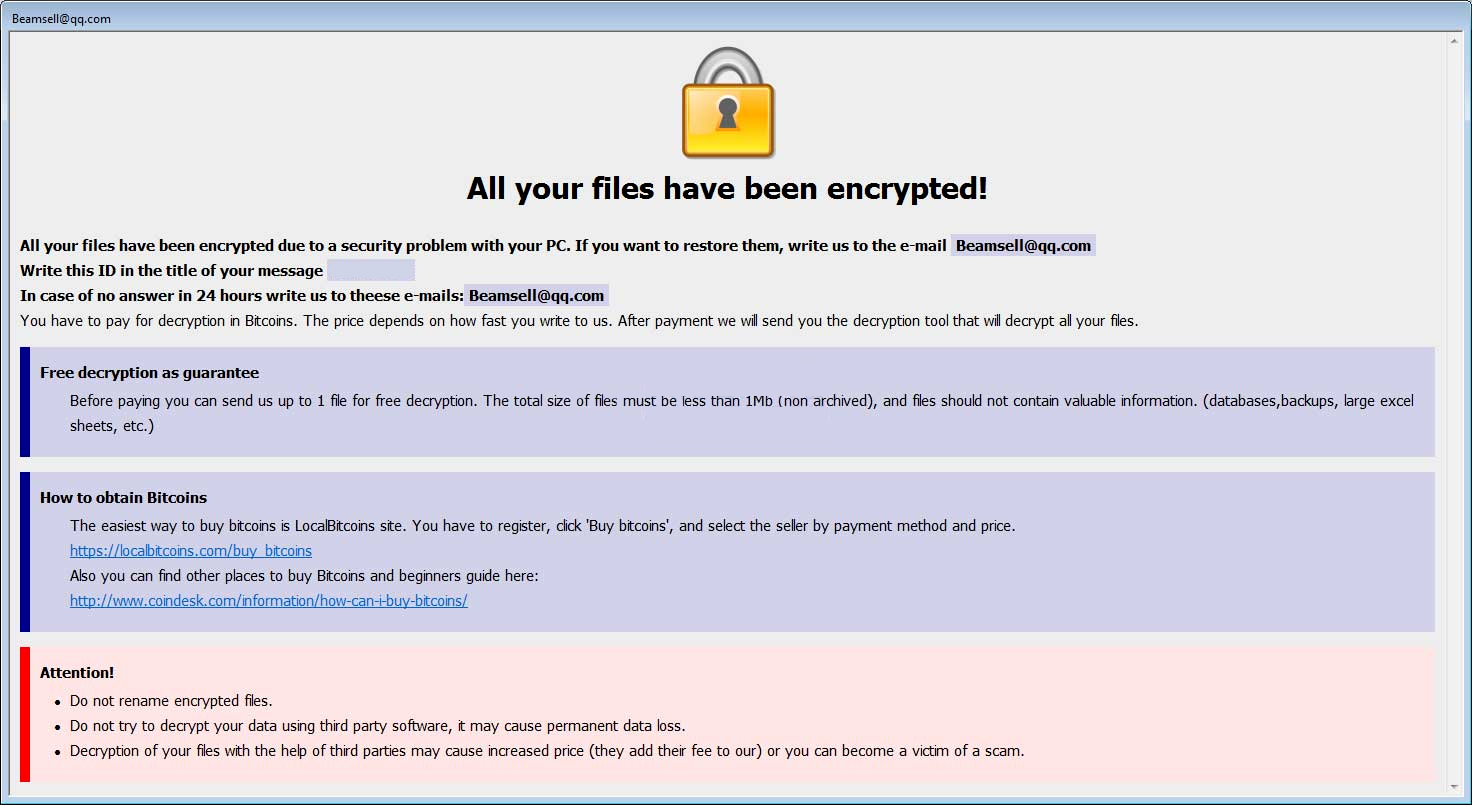
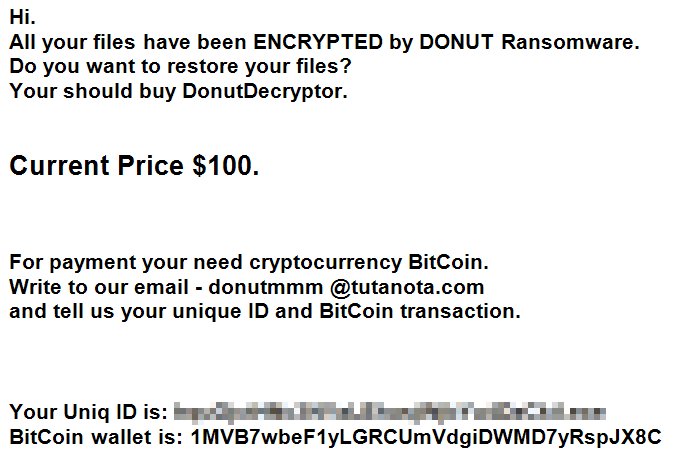
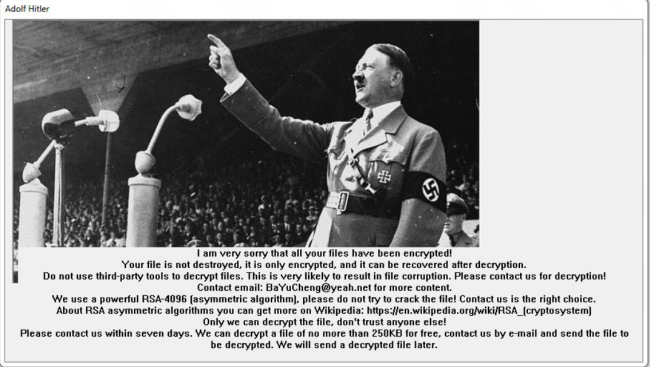
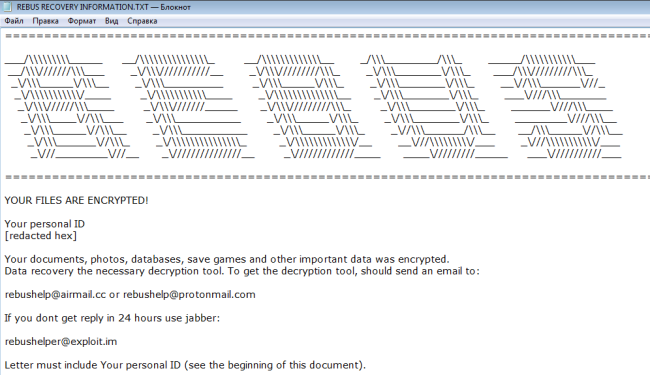
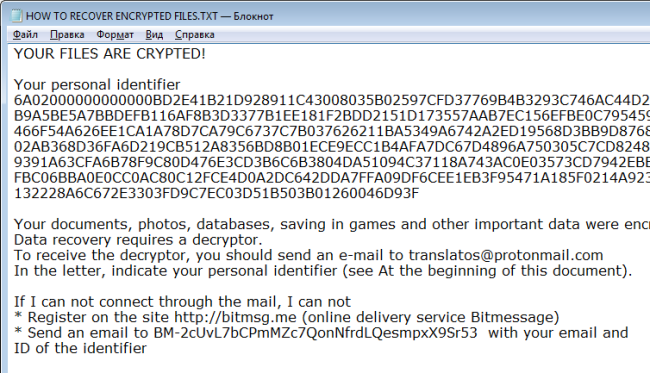
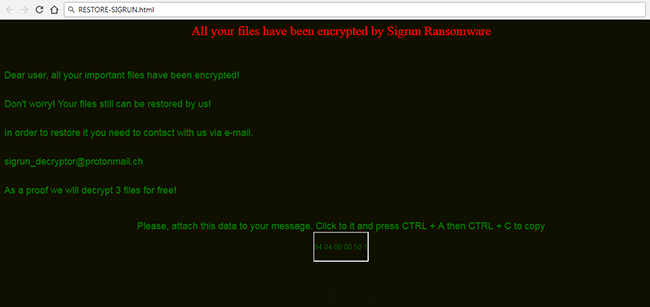
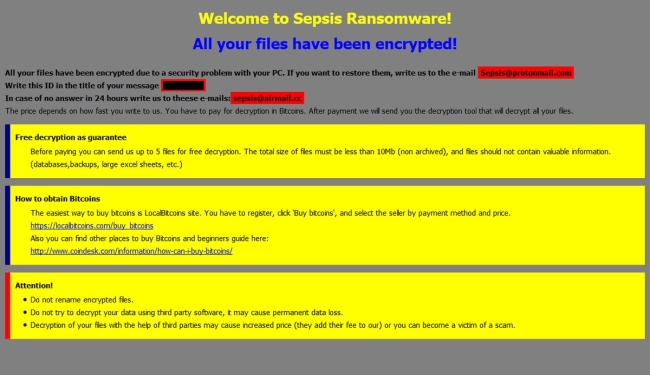
How to remove Gandcrab 4 ransomware and restore .KRAB files
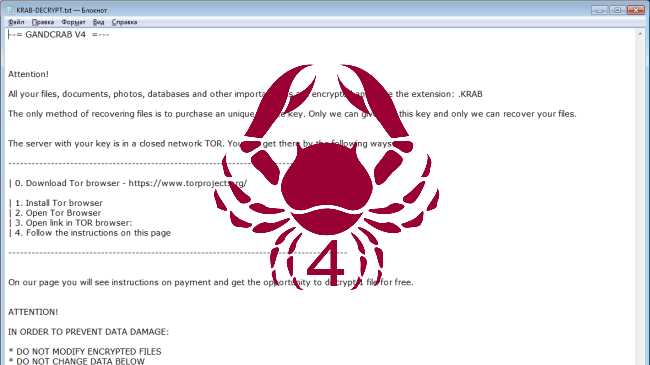
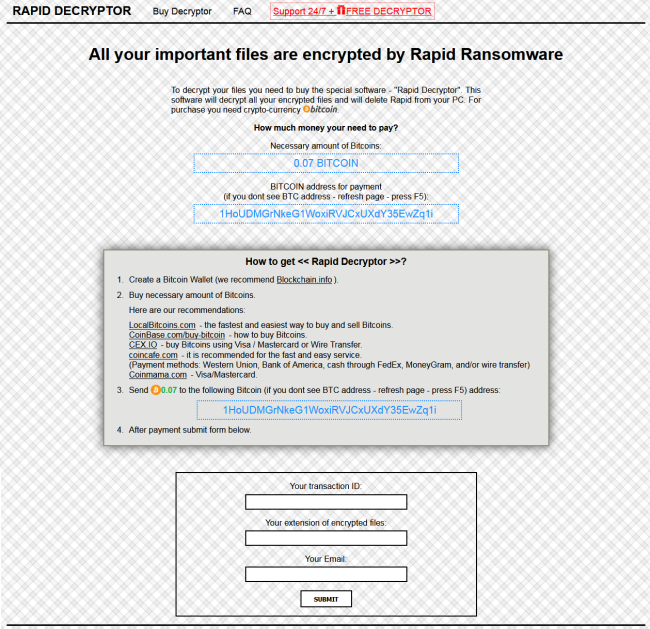
Gandcrab 4 is another ransomware-type virus from Gandcrab developers. The fourth version of the virus operates like previous ones: once it gets on victim’s computer, the virus starts encryption procedure. Upon completion of the encryption process, Gandcrab 4 Ransomware blackmails user into giving him money for data recovery.