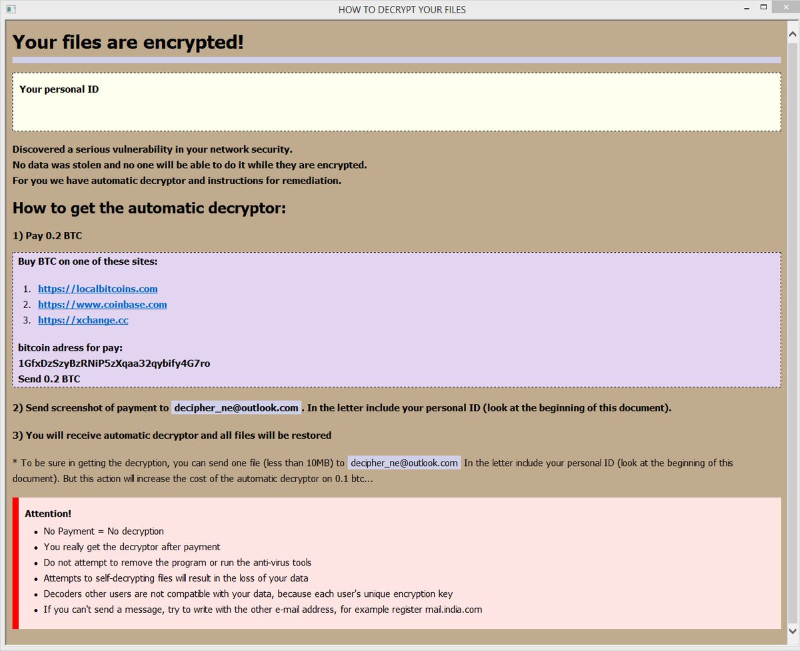
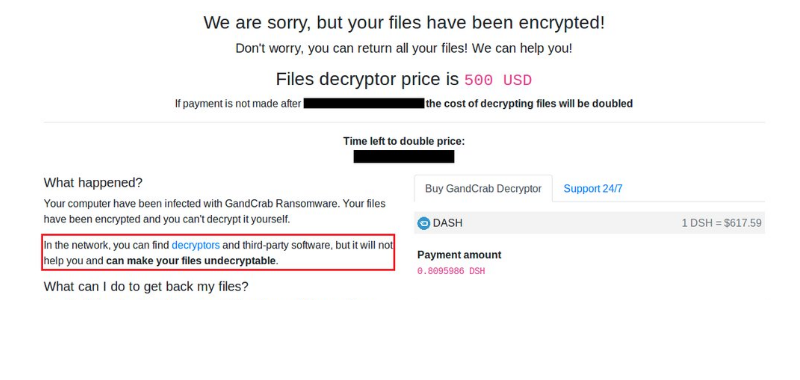
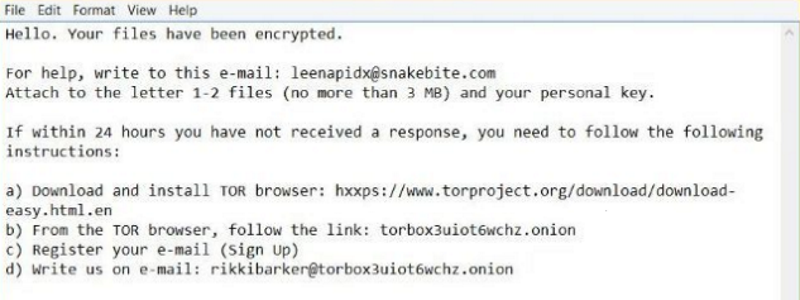
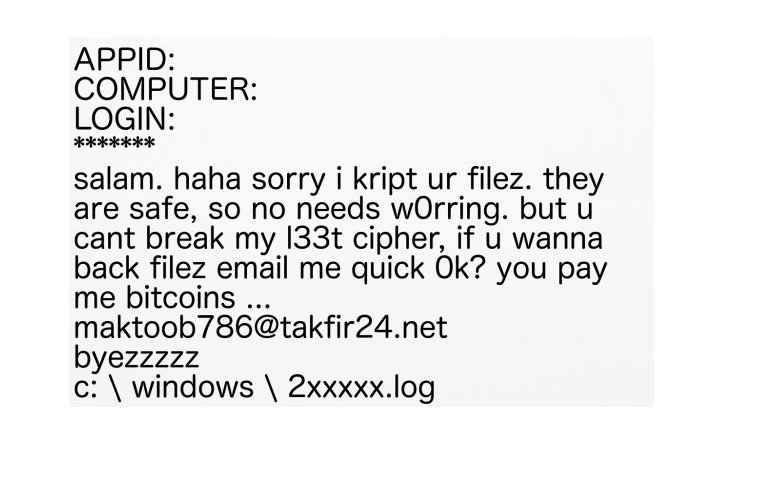
How to remove B2DR Ransomware and decrypt .bronmerkberpa1976@protonmail.com.b2dr files
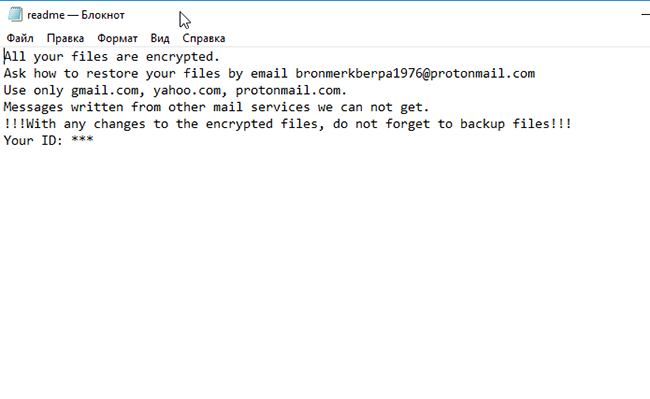
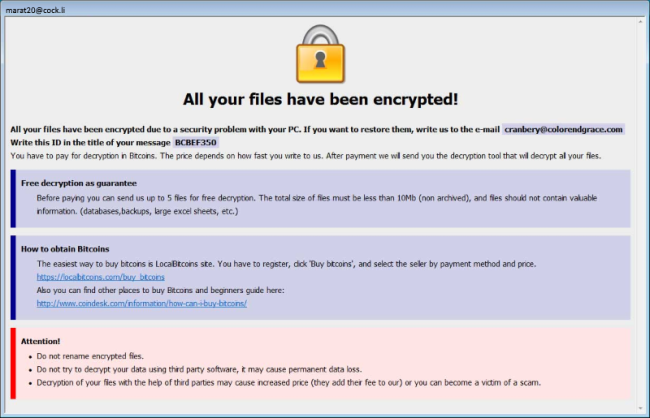
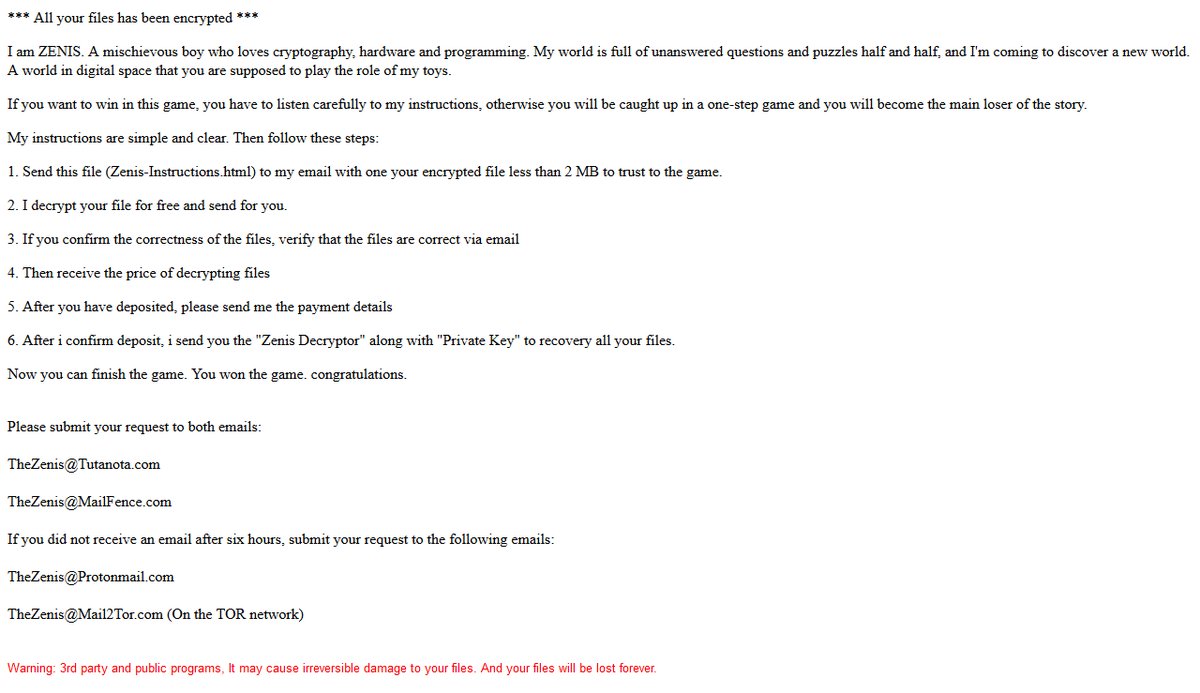
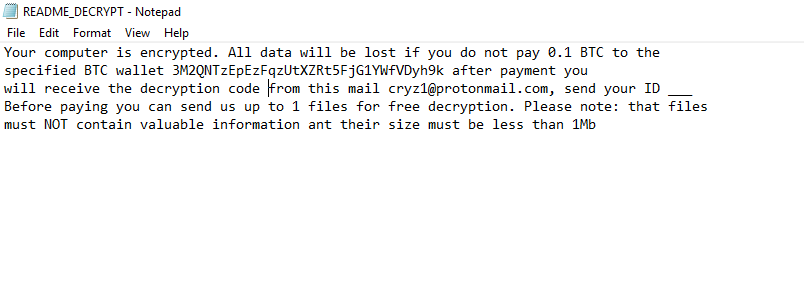
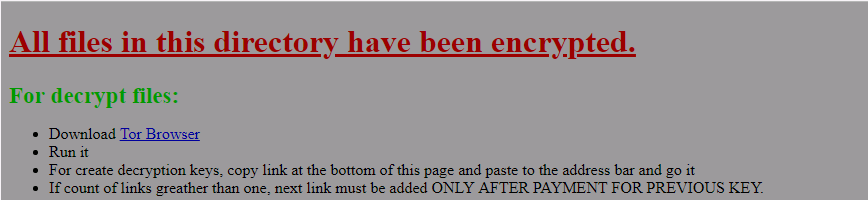
B2DR Ransomware is a fresh threat released in March 2018 that already infected many computers. Following infiltration, it encrypts user’s personal files adding .bronmerkberpa1976@protonmail.com.b2dr extension to all infected files. Like other such viruses, it leaves short instruction (readme.txt) on how to restore your files for the completion of its work.