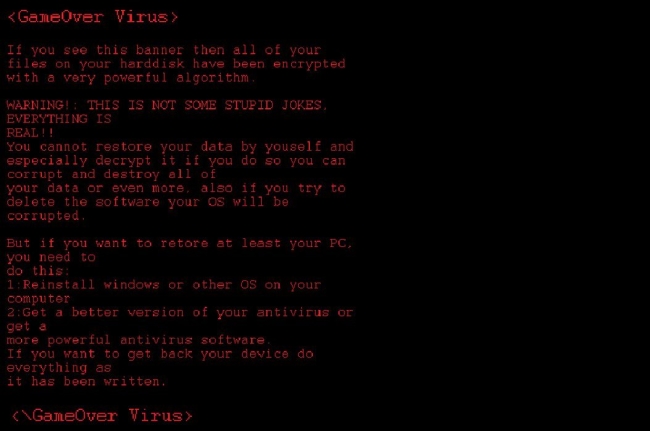
What is GameOver Ransomware?
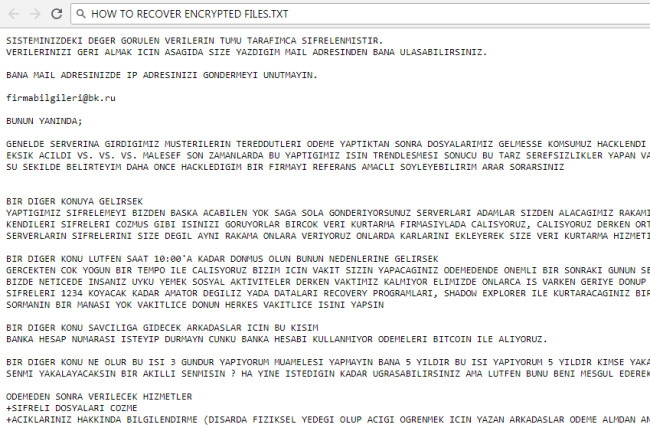
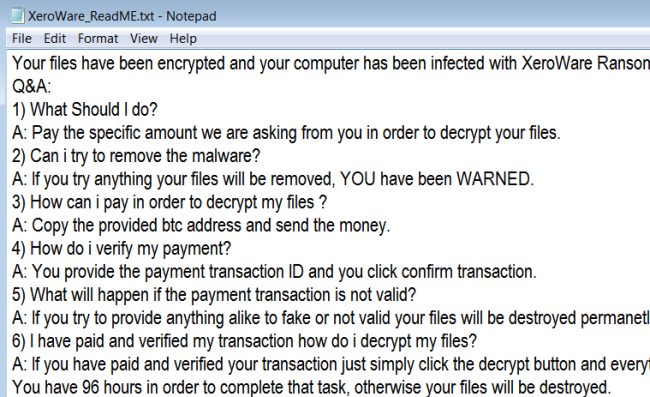
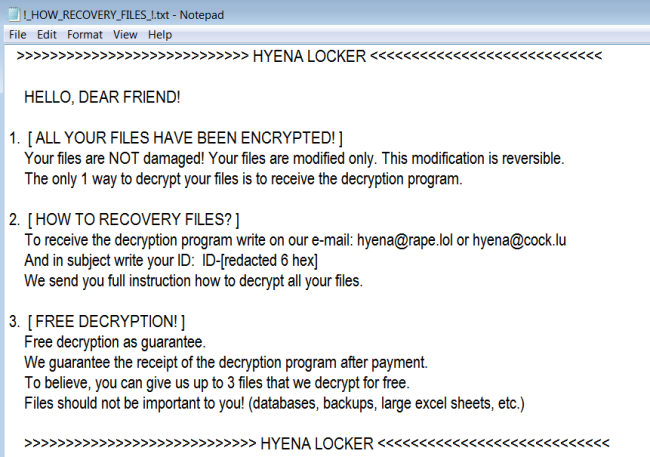
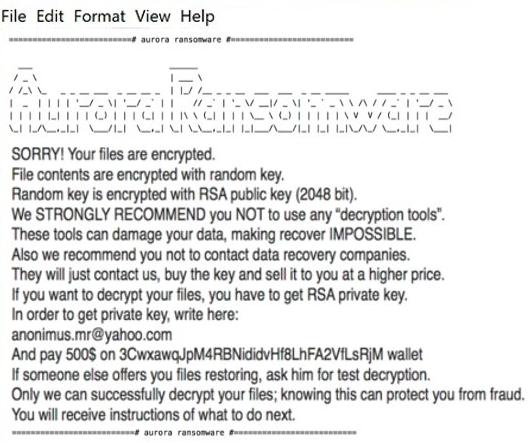
GameOver is a new cryptotrojan which came out on July, 2018. This malware encrypts user data and then extorts money. Lately, such cyber-attacks have become more frequent, this is due to an easy mark to hit up for money and at the same time remain anonymous avoiding any punishment. The encryption process goes unnoticed and once it is done, all user files become inaccessible. To get back your files, you are forced to pay a sum of money in bitcoins. Actually, if you have been attacked by GameOver Ransomware, there is no need to contact them and especially to make any concessions. Remember, you are up against fraudsters who don’t care about your files and whose the main purpose is to make a profit. Hence, there is a high risk of being left without decryptor and money. Instead, you may try using this guide to remove GameOver Ransomware and decrypt .gameover files without spending any money. read more