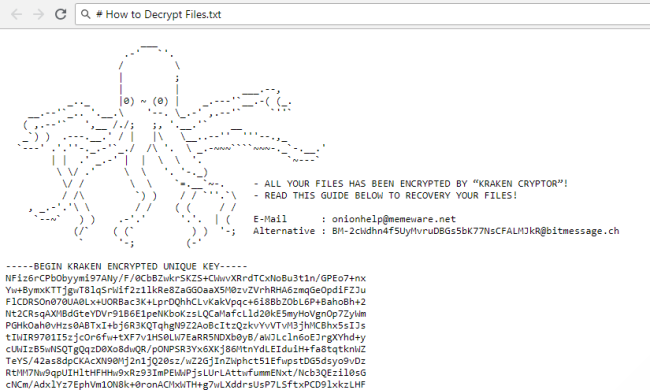
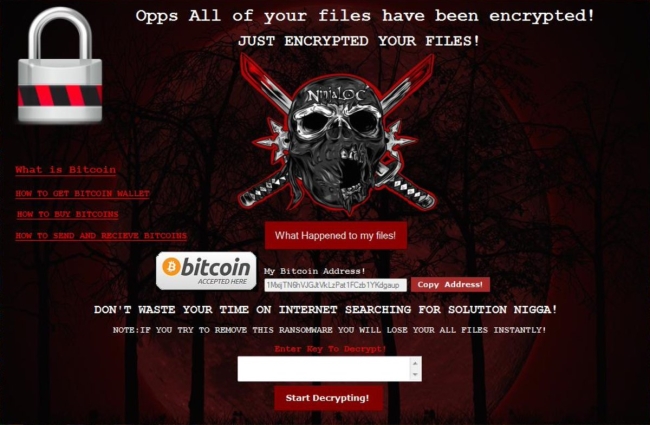
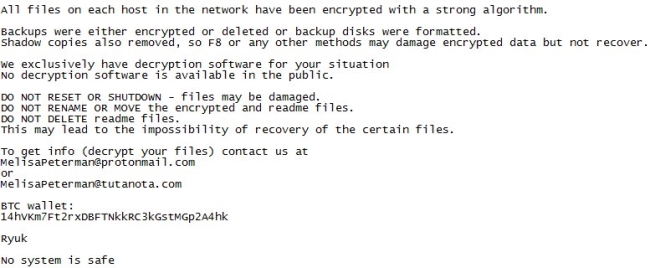
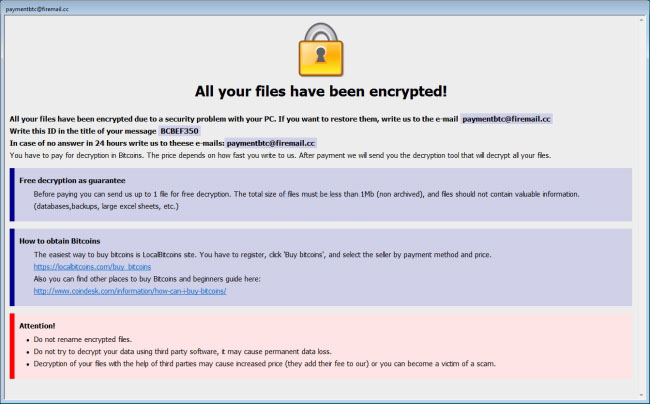
How to remove Waifu Ransomware and decrypt .waifu files
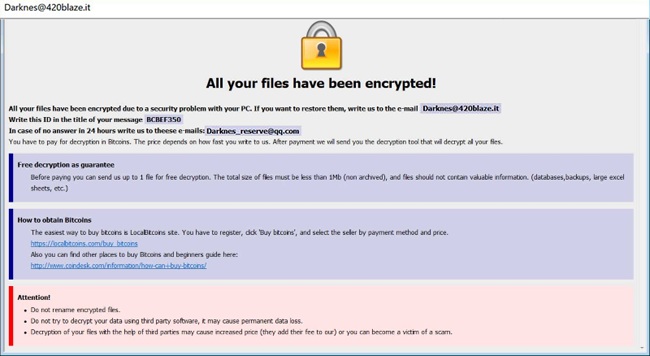
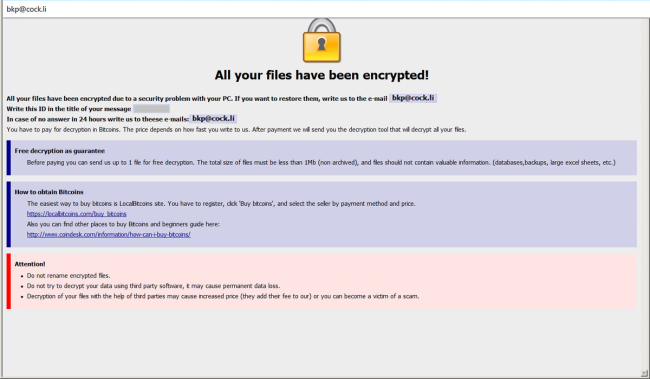
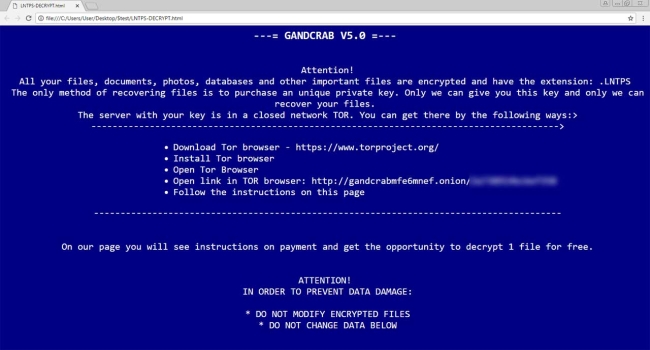
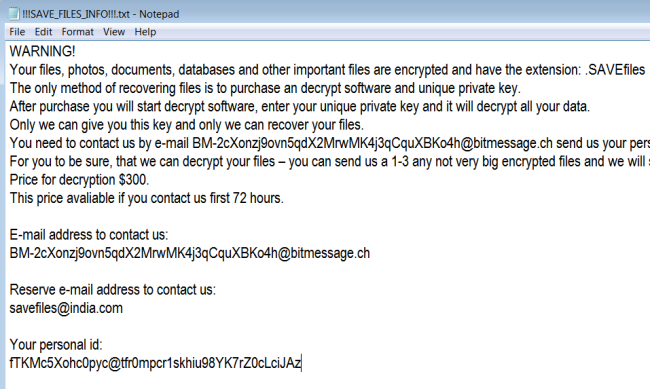
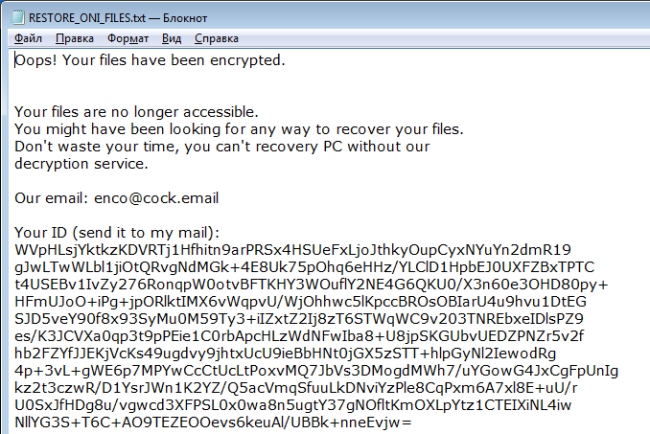
Waifu is a new malware which is originated from Dharma family. If you are not familiar with Dharma virus, you should know that this is a dangerous virus that encrypts data on the infected computer and then demands a ransom. The ransom amount is not public (cybercriminals usually demand $500-$1000 in Bitcoins), it is established individually after the user sends them assigned ID number.