What is TeslaCrypt?
Teslacrypt is a ransomware application that was released in February 2015. The ransomware is designed to infect all versions of Windows existing at the moment. Settled on a victim’s system TeslaCrypt makes changes on a system level, which start with disabling of Windows Task Manager, Regedit and Command Prompt tools. Blocking of these utilities is aimed to complicate the removal process and to tighten the pressure showing the user that the computer is totally under the control of the ransomware. Alongside with that TeslaCrypt adds its files to the Application Data folder as well as several registry entries to the registry. Finally, the ransomware scans all drive letters for the files with specific extensions that are to be encrypted. It’s noteworthy that TeslaCrypt will look for data on all drivers including removable, network folders and DropBox locations.
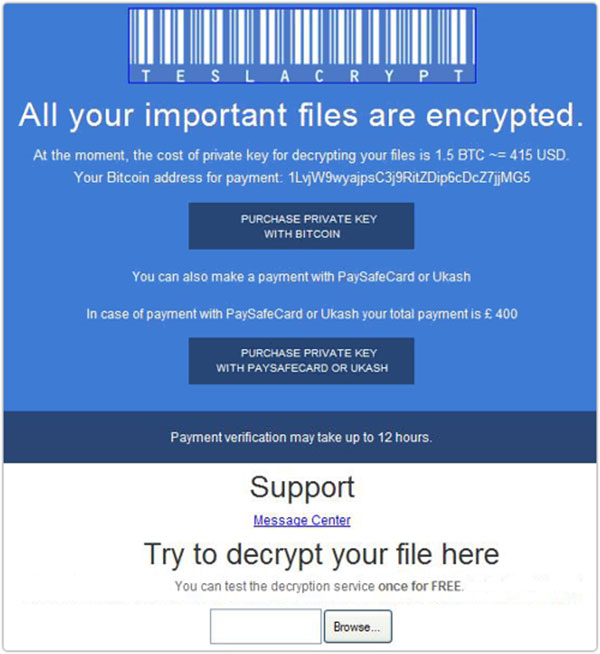
The algorithm Teslacrypt uses is AES-256 code, though the wallpaper and the notes of the ransomware may state different. The affected files become inaccessible and gain the extension that varies due to the Teslacrypt version. Alongside with file ciphering TeslaCrypt will add a text note to every location containing encrypted files, as well as change your wallpaper and add a note to your desktop. There you will see several URLs to Decryption Service site with the stated amount of ransom and corrupted files.
What to do if your PC is infected with TeslaCrypt
As soon as you notice the presence of the ransomware on your system, you should turn your computer off. If it is possible try to create a backup or image of your hard drive info. This may let you to reserve the state of your drives in case a decryption method would be created afterwards.
How TeslaCrypt got installed on your computer
The strongest chances to get TeslaCrypt virus is via malicious sources. Usually these are hacked by malware developers sites that now use exploit kits. Exploit kits is software that employs weak spots of your programs. After an exploit kit sneaks into your computer it is capable of installing and launching the ransomware without user’s knowledge.
Symptoms of TeslaCrypt infection
It’s difficult not to notice ransomware, since it often has one of the processes responsible for displaying a notification message. This window blocks the screen leaving the user minimum alternatives. Besides, some files will be inaccessible, as in many cases ransomware encrypts them to exasperate the scaring effect.
How to remove TeslaCrypt?
To make sure that the adware won’t reappear, you need to delete TeslaCrypt completely. For this you need to remove the files and registry entries of the ransomware. We should warn you that performing some of the steps may require above-average skills, so if you don’t feel experienced enough, you may apply to automatic removal tool.
Performing an antimalware scan with Norton would automatically search out and delete all elements related to TeslaCrypt Ransomware. It is not only the easiest way to eliminate TeslaCrypt Ransomware, but also the safest and the most assuring one.
Steps of TeslaCrypt manual removal
Restart Windows in Safe Mode
For Windows 7, 8, XP and Vista:
- Restart the system
- While computer is rebooting press F8 several times
- In the appeared list of options choose Safe Mode
For Windows 10:
- In the Start menu click on the power button
- Hold Shift and choose Restart
- Choose Troubleshoot
- In the Advanced Options choose Startup Settings
- Click Restart
- Select Enter Safe Mode With Networking
Delete files and registry entries added by TeslaCrypt
Now you will be able to reach the needed functions and files. For eliminating the ransomware activity, you need to find all of the following items and delete them.
Remove TeslaCrypt files and folders:
%AppData%\.exe
%AppData%\key.dat
%AppData%\log.html
%LocalAppData%\.exe
%LocalAppData%\storage.bin
%LocalAppData%\log.html
%Desktop%\Save_Files.lnk
%Desktop%\CryptoLocker.lnk
%Desktop%\HELP_TO_DECRYPT_YOUR_FILES.bmp
%Desktop%\HELP_TO_DECRYPT_YOUR_FILES.txt
%Desktop%\HELP_TO_SAVE_FILES.txt
%Desktop%\HELP_TO_SAVE_FILES.bmp
%Documents%\RECOVERY_FILE.TXT
%Desktop%\HELP_RESTORE_FILES.bmp
%Desktop%\HELP_RESTORE_FILES.txt
HELP_RESTORE_FILES_.TXT
Remove TeslaCrypt registry entries:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\AVSvc %AppData%\.exe
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\crypto13 %AppData%\.exe
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\AVrSvc %LocalAppData%\.exe
HKCU\Control Panel\Desktop\Wallpaper "%Desktop%\HELP_RESTORE_FILES.bmp"
HKCU\Control Panel\Desktop\Wallpaper "%Desktop%\HELP_TO_DECRYPT_YOUR_FILES.bmp"
HKCU\Control Panel\Desktop\Wallpaper "%Desktop%\HELP_TO_SAVE_FILES.bmp"
Restore the files encrypted by TeslaCrypt
Use the decrypting tool
Some time after the spread of TeslaCrypt the decryption tool was released. TeslaDecoder is capable of handling the files with .ECC, .EXX, and .EZZ extensions. You can download the decryption tool here. To use it simply extract the archive and run the TeslaDecoder.exe file. When launched the tool will scan storage.bin, key.dat and Windows Registry for a key. If it manages to detect the key, the utility will inform user that it can start decryption. Otherwise you can input the path to storage.bin or key.dat files manually.
We advise to run a test decryption first before launching a full operation. For this replace an encrypted file into a new folder and click Decrypt Folder. If the process goes smoothly, then you can proceed to the Decrypt All option.
Restore the system
- Initiate the search for ‘system restore’
- Click on the result
- Choose the date before the infection appearance
- Follow the on-screen instructions
Roll the files back to the previous version
- Right-click the file and choose Properties
- Open the Previous Version tab
- Select the latest version and click Copy
- Click Restore




