How to remove Startgo123.com

Startgo123.com may take place of your search engine and homepage after browser hijacker penetration. Don’t be alarmed, browser hijacker is not a virus, it’s small application which is used to generate advertising profit. However, this doesn’t mean that your system is safe. Following infiltration, it starts to modify the browser’s configuration without user’s agreement and participation.
How to remove Malware Crusher
Malware Crusher is promoted as a superior anti-malware tool capable of fighting diverse computer infections. In reality, it’s a potentially unwanted program that displays fake threats to make the user pay money. The thing is that free version can’t fix detected problems, instead, it offers to buy the license of Malware Crusher.
How to remove Fastsearch.me
How to remove Mediplayclassic.info
What is Mediplayclassic.info?
Mediplayclassic.info belongs to the potentially unwanted program, but it is not a viral program as most people got used to think. It’s just a hijacker that is able to spoil users’ experience on the Internet. Once installed, it will get your browser configurations spoiled to fill your browser with sponsored content. It alters and changes search results without any permission so that you can’t actually find anything useful but the tons of advertisement. This is quite unpleasant because even if you try to get rid of Mediplayclassic.info and change your homepage, it will come back and become your homepage again and again.
How to remove Obtenez Email New Tab
Obtenez Email New Tab may appear on your browser after you install some freeware. This extension itself is installed automatically as an optional offer if a user doesn’t uncheck it. Following successful penetration, it starts making changes to system and browser configuration to spoil users’ experience on the web.
How to remove Pushstat.com
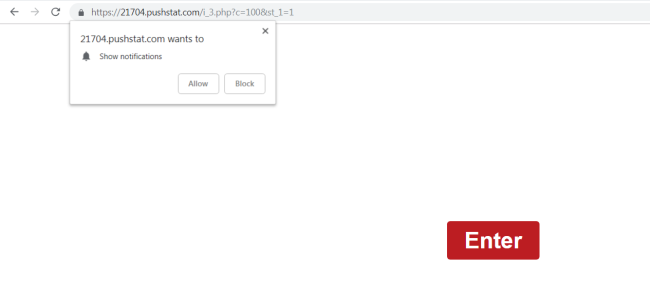
Pushstat.com is an ad-supported domain that may open on users’ browsers periodically as a result of adware getting installed on their computers. Pushstat.com and its subdomains (p4c0.Pushstat.com, tk3v.Pushstat.com, f1ub.Pushstat.com, and others) ask users to allow Pushstat.com to send them notifications.
How to remove Bkp Ransomware and decrypt .bkp files
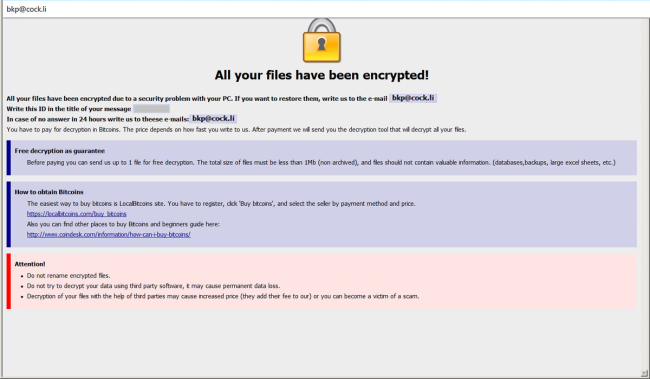
Bkp is the name of malware that aims to lock users’ data via encryption. When the encryption process is finished, the virus demands ransom for decrypting data by threatening to delete them all in case of non-payment. The ransom amount is not public (cybercriminals usually demand $500-$1000 in Bitcoins), it is established individually after the user sends them assigned ID number.
How to remove Private.searchmedia.club

What is Private.searchmedia.club?
Private.searchmedia.club is a deceptive search site that allegedly maintains users’ privacy while browsing Internet. This way, developers aims to attract users who concern about their privacy. Well, I’m sorry to inform you that Private.searchmedia.club actually collects personal information related to users’ browsing habits. This is all aimed at delivering suitable advertising content or selling it to third-parties. As a result, your browser will be filled up with various pop-up advertisements and frequent redirects.
How to remove MM Unzip

MM Unzip is a sneaky application for Mac computers, which, along with declared functions, takes advantage of users’ computers for advertising puproses. It mostly penetrates system bundled with other freeware that user may have downloaded from Internet so MM Unzip was hardly installed by user on purpose. After installation, it hijacks web-browsers to display various pop-up advertisements and cause redirections to force users to visit certain sites.