What is Vapor Ransomware?
Vapor is a name of data-kidnapping malware that has started terrorizing users relatively recently. If you haven’t heard of such viruses before, we’ll tell you. Vapor Ransomware is designed with the aim of extorting money from users by encoding important users’ files: images, videos/audio files, and documents. To retrieve data back, the user will have to send a message with personal ID to deadhacksteam@gmail.com, however, we still advise you not to contact them. The point is, a lot of people fall into the trap of this type of scam. There are a lot of cases where cybercriminals do not help their victims, even if they pay up. Remember, you are up against fraudsters so nobody will give any guarantees that they will fulfill their commitments. Hence, there is a high risk of being left without decryptor and money. Instead, you may try using this guide to remove Vapor Ransomware and decrypt .Vapor files without spending any money.
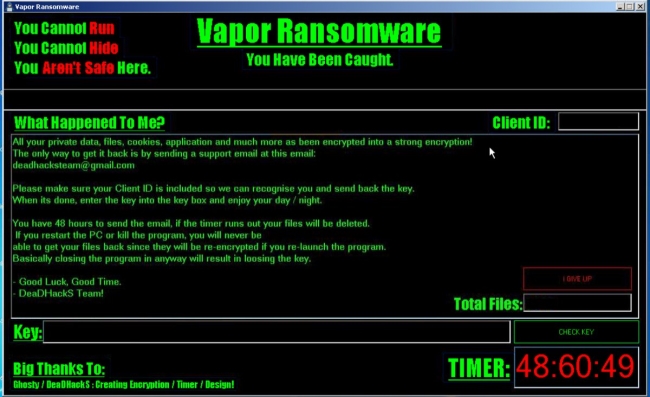
The principle of work of the ransomware is always the same – to encrypt files and then to require payment. Vapor Ransomware encodes users’ personal files using AES encryption algorithm. As a result, each infected file will be renamed and appended with “.Vapor” extension. For example, file “myfamily.jpg” will turn into “myfamily.jpg.Vapor”. Once all the data is encrypted, the ransomware displays lock screen, where the user may find the demands of criminals:
Vapor Ransomware
You Have Been Caught.
—
What Happened To Me?
All your private data, files, cookies, application and much more as been encrypted into a strong encryption!
The only way to get it back is by sending a support email at this email:
deadhacksteam@gmail.com
Please make sure your Client ID is included so we can recognise you and send back the key.
When its done, enter the key into the key box and enjoy your day / night.
You have 48 hours to send the email, if the timer runs out your files will be deleted.
If you restart the PC or kill the program, you will never be able to get your files back since they will be re-encrypted if you re-launch the program.
Basically closing the program in anyway will result in loosing the key.
– Good Luck, Good Time.
– DeaDHackS Team!
Although Vapor is a really dangerous virus, you still have a good chance to get your files back. Before deciphering, you should first stay focused on removing Vapor Ransomware to avoid re-infection. Once Vapor Ransomware is removed, you can proceed with decryption. Both automatic and manual solution is presented here that we hope will help you remove Vapor Ransomware and recover your files.
How Vapor ransomware gets on your PC?
This type of virus can be infiltrated through several methods, including freeware software, spam messages, trojans, software from dangerous sources, etc. A process of installation can start hidden and automatically. Besides that, some malware programs can mark Vapor Ransomware as a trusted software program.
How to remove Vapor ransomware automatically?
To make sure that the ransomware won’t reappear, you need to delete Vapor ransomware completely. For this, you need to remove the files and registry entries of the ransomware. We should warn you that performing some of the steps may require above-average skills, so if you don’t feel experienced enough, you may apply to the automatic removal tool.
Performing an antimalware scan with Norton would automatically search out and delete all elements related to Vapor ransomware. It is not only the easiest way to eliminate Vapor ransomware but also the safest and the most assuring one.
How to decrypt .[old@nuke.africa].Vapor files
Restore files with Stellar Data Recovery
Stellar Data Recovery is an essential tool in the fight against ransomware-type viruses that can recover encrypted files.
- Download Stellar Data Recovery and launch it
- Select the drive you want to recover and click START SCAN
- After scanning is finished, you are presented with a list of recoverable files found.
- Select the required files and click the Recover
Decrypt files using our decryption service
You may try using our own service for decrypting files compromised by ransomware-type viruses. The analysis of data takes 3-5 days, after which, we will let you know whether it’s decryptable or not. Note: the service is paid, payment is charged only for decryption, the analysis is free. In order to use our service, you should fill out the form listed below.
Also, please add a log file, created on your PC:
- Click “Start” and type: “cmd.exe” in the search box
- Right-click “cmd.exe” and select “Run as administrator“
- In command line, type or copy/paste following: dir C:\ /a/s > “%userprofile%\dirc.log”
- Find and attach the created “%userprofile%\dirc.log” file to the web form
Please attach encrypted text files according to the following conditions:
- number of files should not exceed 4;
- file size is not more than 8 megabytes;
- files must be from different folders;
- files must be unique.
Restore the system
- Initiate the search for system restore
- Click on the result
- Choose the date before the infection appearance
- Follow the on-screen instructions
Roll the files back to the previous version
- Right-click the file and choose Properties
- Open the Previous Version tab
- Select the latest version and click Copy
- Click Restore
If the above-mentioned methods didn’t help in eliminating the threat, then it’s better to rely on an automatic way of deleting Vapor Ransomware.
How to prevent ransomware infection
To prevent infection with ransomware-type viruses, you should have proper antimalware software. This method is convenient because it allows you to detect a virus before it penetrates, and therefore to avoid infection and the loss of all your data. It is capable of protecting not only home computers but also server systems in large organizations. Download antimalware program to secure your system and privacy.




