How to remove Troldesh ransomware and decrypt .xbtl files

What is Troldesh ransomware?
Troldesh ransomware is known as a serious threat for a while now – it has released several versions and keeps updating. Like any typical ransomware, it is able to detect and cipher all popular types of files. After hijacking the data, it alerts the victim with a warning that appears as a wallpaper. The message states the encryption and gives Tor addresses to revert it. No need to say that it can be done only after a victim transfers money to the cyber criminals. We would like to emphasize the weakness of the deal, as the scammers don’t provide any guarantees. Instead of paying the ransom to unknown sources, it’s better to find the ways and concentrate on how to remove Troldesh ransomware and decrypt .xbtl files on your own.
How to remove Crysis ransomware and decrypt .crysis files
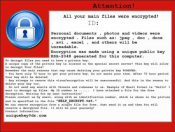
Crysis ransomware is one of the versions of the diverse threat known as virus-encoder. The same as any other typical ransomware, Crysis encryption virus infiltrates system stealthily and takes your data as a hostage. For retrieving your photos, media files and documents the creators of Crysis ransomware demand a certain amount of money after paying which you will get the decrypting application. Or so they say. In fact, there are no guarantees that the scammers will stand by their promise.
How to remove Counterflix ads
We guess all of us find it disappointing when a site of an interest is blocked due to location policies, So, it’s not surprising that some users try to overcome these restrictions with the help of additional software and services. Counterflix is the name of one of such tools that offer prospects of granting the access to the restricted sources. The service solicitously presents its DNS servers to bypass the interdictions,
How to remove Bhd4.xyz redirections

Seeing the bhd4.xyz page on your web browser as the first thing after it launches is an indicator of a wicked infection. This malware is an ad-supported application that will by all means possible lure user to the sites of sponsors. It will occupy the browser not only by producing pop-ups, but also by forcing redirections to the bhd4.xyz source and then to one of the affiliates.
How to remove Altrk2.com page
Altrk2.com is a page that may infect your browser and then annoy you a lot with sudden redirections. While the infection is on your system, a simple click on a random space on a safe site will result in opening Altrk2.com source. The site is presented as a blog with articles on various themes, however, their main goal is to promote some products, which often turn out to be another malware.
How to remove Tavanero.info page
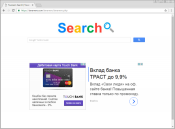
Tavanero.info is a browser hijacker that, identically to many other dangers of that kind, use the disguise of a search engine. In the design it strongly resembles Google search page, however its details expose the deception themselves. Halfway the malicious identity becomes obvious because the page https://tavanero.info/tavanero/tavanero.php appears on browsers without invitation or a word of warning, halfway because of ad banners flashing below the search bar.
How to remove Thor ransomware and decrypt .thor files
Thor ransomware is a encrypting successor of ill-famed Locky ransomware, a threat that already has many variants. However, it significantly differs from previous editions of the virus. First of all, it combines RSA and AES ciphers, which makes decryption of files way more difficult than before. Second, now it is capable of scattering over 400 file types. Altogether these factors make the malware a serious hazard to information safety.
How to remove Hallmark eCard scam
How to remove hao.7654.com page
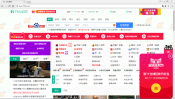
Hao.7654.com is a threat of a browser hijacker group that is characterized by capturing control over browser settings. This is reflected in changing the main page and search domain to hao.7654.com. Nevertheless the page is of Chinese origin, the malware doesn’t affect only Chinese users, and has spread through the globe very fast.