How to remove Arberittertwa.info
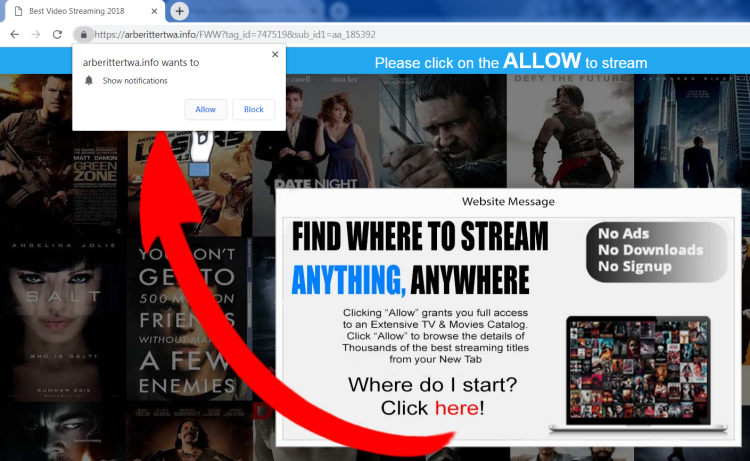

What is Arberittertwa.info?
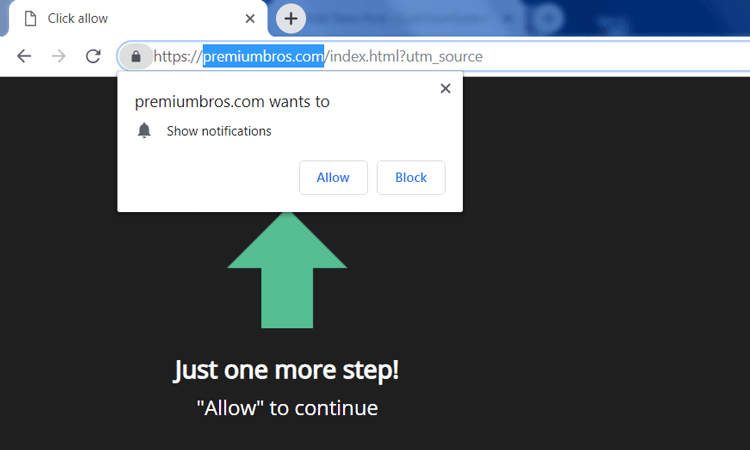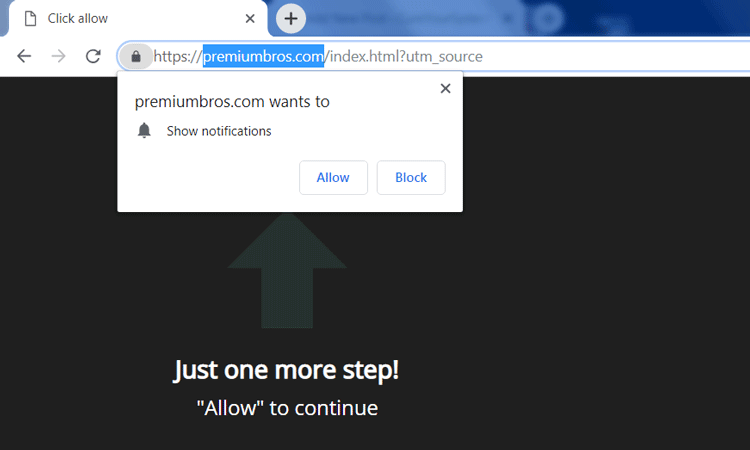
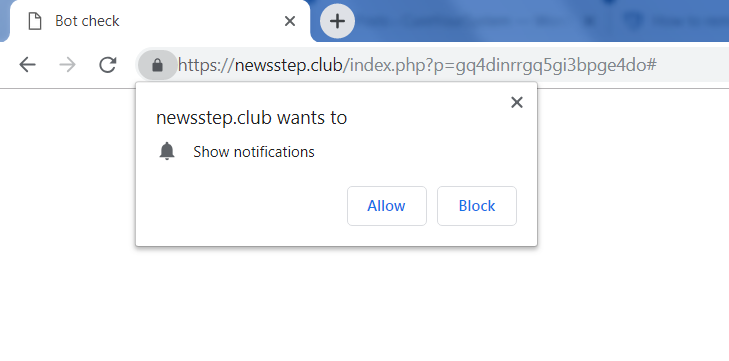
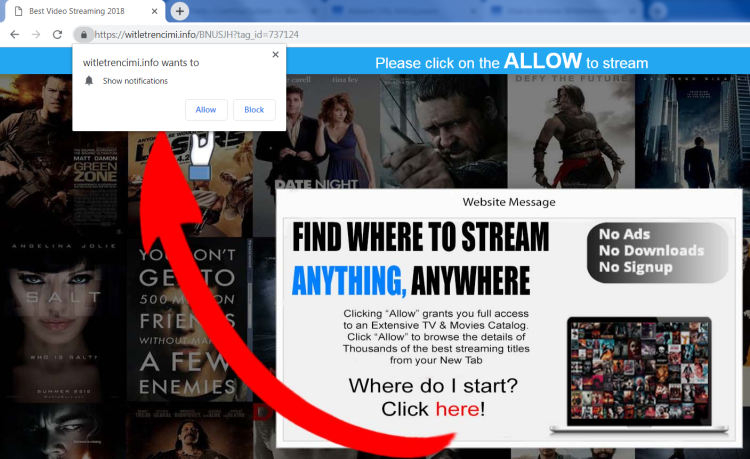
Arberittertwa.info is a spam web page that will pop-up on a browser in case of adware infection. You may have picked up the malware while installing some questionable program from the Internet. Once inside, it will display ads and offer to turn on notifications. Do not try to click on “Allow Notifications”, as it may result in getting more malware on your computer. Therefore, you should remove Arberittertwa.info Adware as soon as possible.
- How to remove Arberittertwa.info Automatically
- Remove Arberittertwa.info from Programs and Features
- Remove Arberittertwa.info Adware from browsers
- Delete Arberittertwa.info pop-ups and notifications on Android
How to remove Arberittertwa.info automatically:
The easiest and convenient way to get rid of malware is to use a proper anti-malware program that can eliminate Arberittertwa.info and all its traces in just a few clicks.