What is HPE iLO Ransomware?
HPE iLO is a new ransomware-type virus that encrypts data on server systems HPE iLO 4. Notably, the distribution method is very different from many similar viruses. To get into victims’ computers, cybercriminals exploit remote control system (HPE Integrated Lights-Out). After this, they mount malicious ISO image into computers, by opening which, the encryption process is activated. Upon completion, it displays a lock screen informing that your files have been encrypted and next steps to get them back. Below you will find a step-by-step guide to remove HPE iLO Ransomware and recover your files.
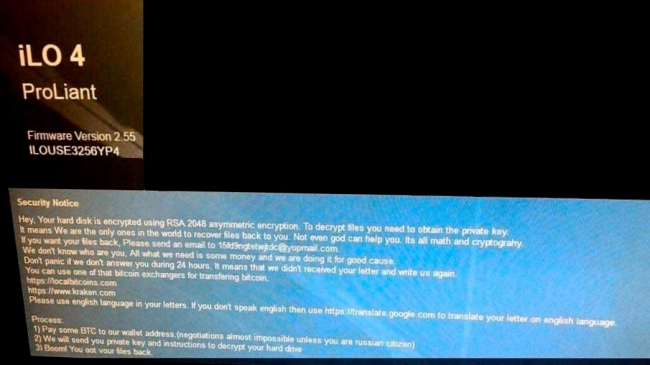
The amount of ransom is not small, 2 bitcoins (~18 559.45 USD). We suggest that cybercriminals expect to get money from corporate organizations so basically they have such server systems. To complicate matters further, HPE iLO Ransomware also deletes all shadow copies of files which are necessary for data restore. Despite this, we still urge you not to contact them as it’s fraught with money loss. The thing is that malefactors often disappear once money is transferred. But, don’t despair, the virus doesn’t delete your files which means you have a good chance to get them back. First, you need to remove HPE iLO Ransomware and then try to use one of the decryption tools provided here. Here you’ll find a detailed instruction which, hopefully, will help you.
How HPE iLO ransomware gets on your PC?
This type of virus can be infiltrated through several methods, including a freeware software, spam messages, trojans, software from dangerous sources, etc. A process of installation can start hidden and automatically. Besides that, some malware programs can mark HPE iLO Ransomware as a trusted software program.
What to do if your PC is infected with HPE iLO ransomware
As soon as you notice the presence of the ransomware on your system, you should turn your computer off. If it is possible to try to create a backup or image of your hard drive info. This may let you to reserve the state of your drives in case a decryption method would be created afterward.
How to remove HPE iLO ransomware?
To make sure that the ransomware won’t reappear, you need to delete HPE iLO ransomware completely. For this, you need to remove the files and registry entries of the ransomware. We should warn you that performing some of the steps may require above-average skills, so if you don’t feel experienced enough, you may apply to automatic removal tool.
Performing an antimalware scan with Norton would automatically search out and delete all elements related to HPE iLO ransomware. It is not only the easiest way to eliminate HPE iLO ransomware but also the safest and the most assuring one.
How to decrypt and restore files
Restore files with an automatic tool
There is a possible way to decrypt files encrypted by HPE iLO Ransomware using Data Recovery Pro that would help you recover your files in the absence of required decryptor.
- Download Stellar Data Recovery and launch it
- Select the drive you want to recover and click START SCAN
- After scanning is finished, you are presented with a list of recoverable files found.
- Select the required files and click the Recover
Decrypt files using our decryption service
You may try using our own service for decrypting files compromised by ransomware-type viruses. The analysis of data takes 3-5 days, after which, we will let you know whether it’s decryptable or not. Note: the service is paid, payment is charged only for decryption, the analysis is free. In order to use our service, you should fill out the form listed below.
Also, please add a log file, created on your PC:
- Click “Start” and type: “cmd.exe” in the search box
- Right-click “cmd.exe” and select “Run as administrator“
- In command line, type or copy/paste following: dir C:\ /a/s > “%userprofile%\dirc.log”
- Find and attach the created “%userprofile%\dirc.log” file to the web form
Please attach encrypted text files according to the following conditions:
- number of files should not exceed 4;
- file size is not more than 8 megabytes;
- files must be from different folders;
- files must be unique.
Restore the system
- Initiate the search for system restore
- Click on the result
- Choose the date before the infection appearance
- Follow the on-screen instructions
Roll the files back to the previous version
- Right-click the file and choose Properties
- Open the Previous Version tab
- Select the latest version and click Copy
- Click Restore
If the above-mentioned methods didn’t help in eliminating the threat, then it’s better to rely on an automatic way of deleting HPE iLO Ransomware.
How to prevent ransomware infection
To prevent infection with ransomware-type viruses, you should have proper antimalware software. This method is convenient because it allows you to detect a virus before it penetrates, and therefore to avoid infection and the loss of all your data. It is capable of protecting not only home computers but also server systems in large organizations. Download antimalware program to secure your system and privacy.




