How to remove Troldesh ransomware and decrypt .xbtl files

What is Troldesh ransomware?
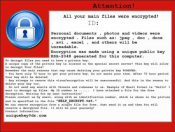
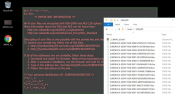
Troldesh ransomware is known as a serious threat for a while now – it has released several versions and keeps updating. Like any typical ransomware, it is able to detect and cipher all popular types of files. After hijacking the data, it alerts the victim with a warning that appears as a wallpaper. The message states the encryption and gives Tor addresses to revert it. No need to say that it can be done only after a victim transfers money to the cyber criminals. We would like to emphasize the weakness of the deal, as the scammers don’t provide any guarantees. Instead of paying the ransom to unknown sources, it’s better to find the ways and concentrate on how to remove Troldesh ransomware and decrypt .xbtl files on your own.