What is GANDCRAB 5.2
GANDCRAB 5.2 is a data-kidnapping malware that encrypts users’ personal files. After encryption, cybercriminals blackmail victims demanding ransom amount of 1200$ in Bitcoins. Moreover, this virus has a timerб and if the user is late on payment, the amount increases to 2400$. By the way, if you have been attacked by GANDCRAB 5.2 Ransomware, there is no need to contact them and especially to make any concessions. Remember, you are up against fraudsters who don’t care about your files and whose main purpose is to make a profit. Hence, there is a high risk of being left without decryptor and money. Instead, you may try using this guide to remove GANDCRAB 5.2 Ransomware and decrypt files without spending any money.

This ransomware mostly penetrates the system via fraudulent emails containing malicious attachments. When the user launches the attached file, the virus starts infecting victim’s data using complicated encryption algorithms. Once all the data is enciphered, ransomware sets new desktop wallpaper:
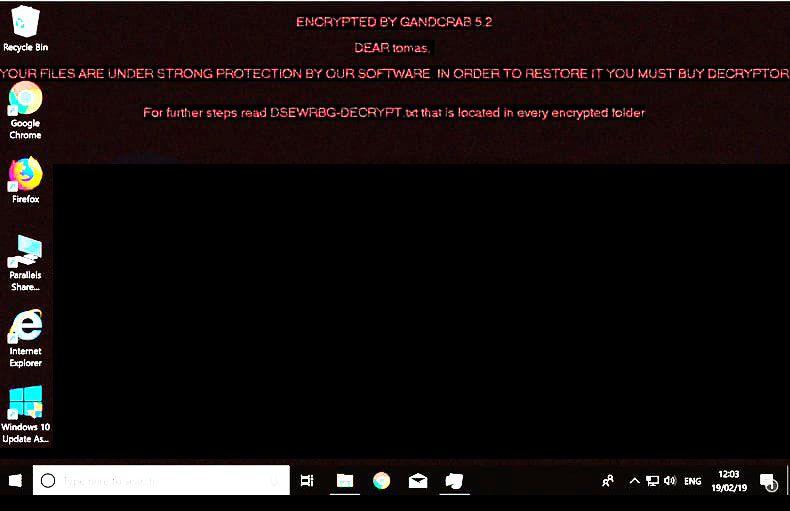
and then drops ransom note [random characters and numbers]-DECRYPT.txt in each folder with the affected files. In our case, the file is called CYYJG–DECRYPT.txt:
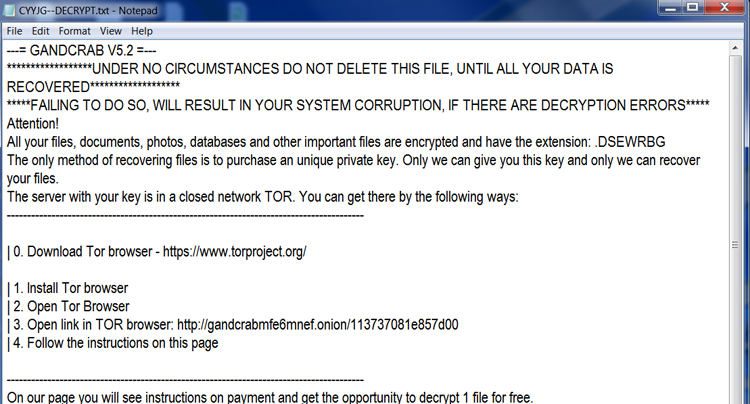
Text presented in the ransom note:
—= GANDCRAB V5.2 =—
******************UNDER NO CIRCUMSTANCES DO NOT DELETE THIS FILE, UNTIL ALL YOUR DATA IS RECOVERED*******************
*****FAILING TO DO SO, WILL RESULT IN YOUR SYSTEM CORRUPTION, IF THERE ARE DECRYPTION ERRORS*****
Attention!
All your files, documents, photos, databases and other important files are encrypted and have the extension: .DSEWRBG
The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
—————————————————————————————-| 0. Download Tor browser – https://www.torproject.org/
| 1. Install Tor browser
| 2. Open Tor Browser
| 3. Open link in TOR browser: http://gandcrabmfe6mnef.onion/113737081e857d00
| 4. Follow the instructions on this page—————————————————————————————-
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW
—BEGIN GANDCRAB KEY—
–
—END GANDCRAB KEY——BEGIN PC DATA—
–
—END PC DATA—
The cybercriminals want the victim to follow hxxp://gandcrabmfe6mnef.onion/**** link via TOR browser (to preserve their anonymity). By clicking on this link, we will see the ransom amount and instructions on how to transfer them money:
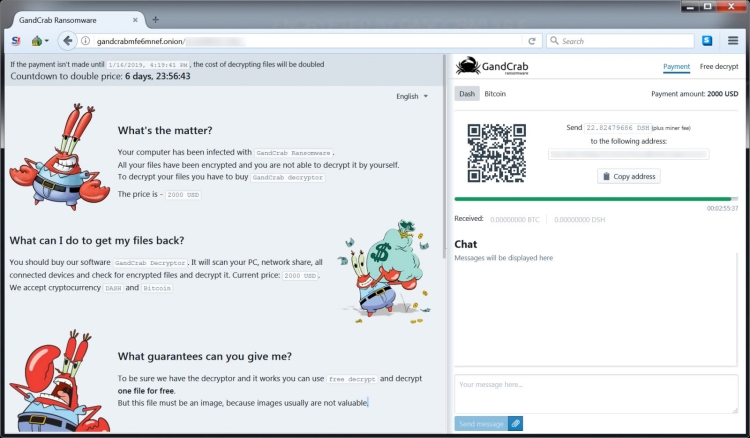
Text presented in this website:
If the payment isn’t made until 1/18/2019, 11:11:06 AM, the cost of decrypting files will be doubled
Countdown to double price: Time is up. Price is doubled!
What’s the matter?
Your computer has been infected with GandCrab Ransomware.
All your files have been encrypted and you are not able to decrypt it by yourself.To decrypt your files you have to buy GandCrab decryptor
The price is – 2400 USD
What can I do to get my files back?
You should buy our software GandCrab Decryptor. It will scan your PC, network share, all connected devices and check for encrypted files and decrypt it. Current price: 2400 USD. We accept cryptocurrency DASH and Bitcoin
What guarantees can you give me?
To be sure we have the decryptor and it works you can use free decrypt and decrypt one file for free.
But this file must be an image, because images usually are not valuable.
I don’t have Bitcoin (BTC) or DASH (DSH). How can I make the payment?
Easy. The list of the most popular exchange services:
BuyBitcoin
CoinMonitor.io
LocalBitcoins
CoinMama
Changelly.com
PAYEER
CEX.IOThe full list of exchange services for Bitcoin here and for DASH here.
Create an account
Charge the balance with a credit card or paypal
Buy requested amount of coins (Bitcoin or DASH)
Make withdrawal to our addressAttention
Don’t delete file *-DECRYPT.txt before full restore of your PC.
Although GANDCRAB 5.2 is a really dangerous virus, you still have a good chance to get your files back. Before deciphering, you should first stay focused on removing GANDCRAB 5.2 Ransomware to avoid re-infection. Once GANDCRAB 5.2 Ransomware is removed, you can proceed with decryption. Both automatic and manual solution is presented here that we hope will help you remove GANDCRAB 5.2 Ransomware and recover your files.
How to remove GANDCRAB 5.2 ransomware?
To make sure that the ransomware won’t reappear, you need to delete GANDCRAB 5.2 ransomware completely. For this, you need to remove the files and registry entries of the ransomware. We should warn you that performing some of the steps may require above-average skills, so if you don’t feel experienced enough, you may apply to the automatic removal tool.
Performing an antimalware scan with Norton would automatically search out and delete all elements related to GANDCRAB 5.2 ransomware. It is not only the easiest way to eliminate GANDCRAB 5.2 ransomware but also the safest and the most assuring one.
How to decrypt files
Restore files with Stellar Data Recovery
Stellar Data Recovery is an essential tool in the fight against ransomware-type viruses that can recover encrypted files.
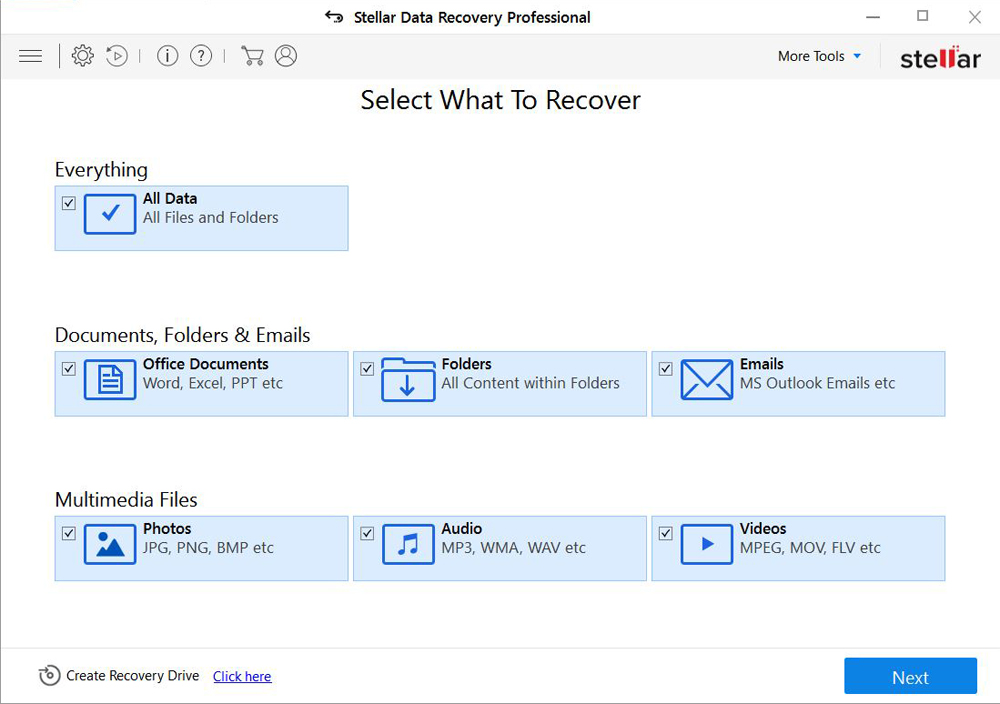
- Download Stellar Data Recovery and launch it
- Select the drive you want to recover and click START SCAN
- After scanning is finished, you are presented with a list of recoverable files found.
- Select the required files and click the Recover
Use decryption tool for Gandcrab Ransomware family
There is a new decryption tool available from Bitdefender Labs that can decrypt files infected by GandCrab versions 1, 4 or 5.
Decrypt files through our decryption service
You may try using our own service for decrypting files compromised by ransomware-type viruses. The analysis of data takes 3-5 days, after which, we will let you know whether it’s decryptable or not. Note: the service is paid, payment is charged only for decryption, the analysis is free. In order to use our service, you should fill out the form listed below.
Also, please add a log file, created on your PC:
- Click “Start” and type: “cmd.exe” in the search box
- Right-click “cmd.exe” and select “Run as administrator“
- In command line, type or copy/paste following: dir C:\ /a/s > “%userprofile%\dirc.log”
- Find and attach the created “%userprofile%\dirc.log” file to the web form
Please attach encrypted text files according to the following conditions:
- number of files should not exceed 4;
- file size is not more than 8 megabytes;
- files must be from different folders;
- files must be unique.
Restore the system
- Initiate the search for system restore
- Click on the result
- Choose the date before the infection appearance
- Follow the on-screen instructions
Roll the files back to the previous version
- Right-click the file and choose Properties
- Open the Previous Version tab
- Select the latest version and click Copy
- Click Restore
If the above-mentioned methods didn’t help in eliminating the threat, then it’s better to rely on an automatic way of deleting GANDCRAB 5.2 Ransomware.
How to prevent ransomware infection
To prevent infection with ransomware-type viruses, you should have proper antimalware software. This method is convenient because it allows you to detect a virus before it penetrates, and therefore to avoid infection and the loss of all your data. It is capable of protecting not only home computers but also server systems in large organizations. Download antimalware program to secure your system and privacy.