What is Locky Ransomware?
Locky Ransomware is a recently appeared example of ransomware. The malware cyphers the files with AES encryption code and later on demands ransom in the sum of 0.5 BitCoins in the exchange for the decryption key. In a while, it operates in a way other ransomware threats do – it appears on a systems and looks for files of certain extensions. As some other ransomware viruses, Locky changes names of encrypted files for making the process of retrieving the data more difficult. The main peculiarity of the ransomware is the ability to encrypt the wider range of files and to affect the files shared within unmapped networks. The practice of ransomware scanning the networks not connected with local drives becomes common for new ransomware threats, so for raising the level of security those should be given the most heavy permissions.
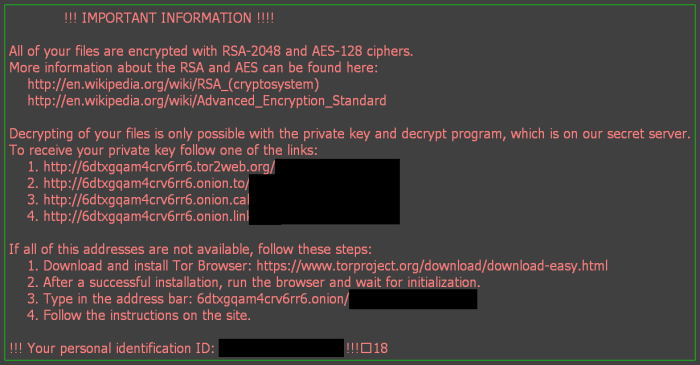
How Locky Ransomware got installed on your computer
The distribution of Locky ransomware simmers down to spam emailing. The messages contain the attachment of a Word document that has a harmful macros. The subject of the emails reads the number of invoice with the appeal to see the attachment. The email persuades users that they have taxes to be paid by the invoice that can be found in attachments. By opening the file a user will see a codified text and a notification that in order to read the text a user should enable the macros. Predictably, turning on the macros initiates a download of Locky Ransomware files.
Symptoms of Locky Ransomware infection
It’s difficult not to notice ransomware, since it often has one of the processes responsible for displaying a notification message. This window blocks the screen leaving the user minimum alternatives. Besides, some files will be inaccessible, as in many cases ransomware encrypts them to exasperate the scaring effect.
How to remove Locky Ransomware?
To make sure that the adware won’t reappear, you need to delete Locky Ransomware completely. For this you need to remove the files and registry entries of the ransomware. We should warn you that performing some of the steps may require above-average skills, so if you don’t feel experienced enough, you may apply to automatic removal tool.
Performing an antimalware scan with Norton would automatically search out and delete all elements related to Locky Ransomware. It is not only the easiest way to eliminate Locky Ransomware, but also the safest and the most assuring one.
Steps of Locky Ransomware manual removal
Restart Windows in Safe Mode
For Windows 7, 8, XP and Vista:
- Restart the system
- While computer is rebooting press F8 several times
- In the appeared list of options choose Safe Mode
For Windows 10:
- In the Start menu click on the power button
- Hold Shift and choose Restart
- Choose Troubleshoot
- In the Advanced Options choose Startup Settings
- Click Restart
- Select Enter Safe Mode With Networking
Delete files and registry entries added by Locky Ransomware
Now you will be able to reach the needed functions and files. For eliminating the ransomware activity, you need to find all of the following items and delete them.
Remove Locky Ransomware files and folders:
MRI6219316107.js
problem.437332391.js
_Locky_recover_instructions.bmp.lnk
Remove Locky Ransomware registry entries:
HKCU\Software\Locky
HKCU\Software\Locky\id
HKCU\Software\Locky\pubkey
HKCU\Software\Locky\paytext
HKCU\Software\Locky\completed 1
HKCU\Control Panel\Desktop\Wallpaper "%UserProfile%\Desktop\_Locky_recover_instructions.bmp"
Restore the files encrypted by Locky Ransomware
Use the decrypting tool
Unfortunately, currently the tool able to decrypt the files infected by Locky Ransomware is not released yet. You may try applying to the methods described below, however, they might not work with the latest versions of Locky Ransomware.
Restore the system
- Initiate the search for ‘system restore’
- Click on the result
- Choose the date before the infection appearance
- Follow the on-screen instructions
Roll the files back to the previous version
- Right-click the file and choose Properties
- Open the Previous Version tab
- Select the latest version and click Copy
- Click Restore




