What is Crysis Ransomware?
Crysis ransomware is one of the versions of the diverse threat known as virus-encoder. It has many versions, different names, and different file extensions that the threat changes the original files to. The list of extensions includes .{mailrepa.lotos@aol.com}.CrySiS, .{TREE_OF_LIFE@INDIA.COM}.CrySiS, .locked, .kraken, .darkness, .nochance, .oshit, .oplata@qq_com, .relock@qq_com, .crypto, .helpdecrypt@ukr.net, .pizda@qq_com, .dyatel@qq_com, _ryp, .nalog@qq_com, .chifrator@qq_com, .gruzin@qq_com, .troyancoder@qq_com, .encrytped, .cry, .AES256, .enc, .hb15. But despite this variety, the same as any other typical ransomware, Crysis encryption virus infiltrates system stealthily and takes your data as a hostage. For retrieving your photos, media files and documents the creators of Crysis ransomware demand a certain amount of money after paying which you will get the decrypting application. Or so they say. In fact, there are no guarantees that the scammers will stand by their promise. Therefore, you should take everything possible to remove Crysis ransomware and decrypt .crysis files before desperately turn to the creators of the malware.
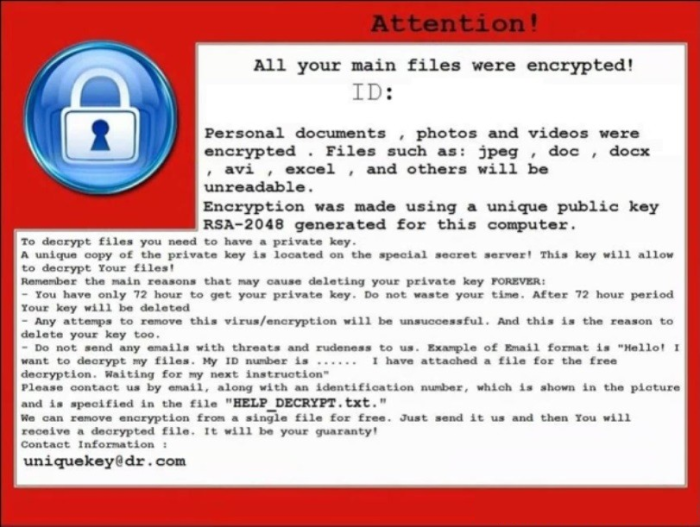
How Crysis Ransomware got installed on your computer
Crysis ransomware is distributed in several approaches. One of which is through email attachments. Once a victim gets a message and opens its attachment, the background installation is triggered and the malware gets into the computer without user’s notice. Other method is by fake software updates. The fraud notifications informing about outdated drivers or applications may emerge while a user browses the net. The messages look like they are generated by the system, however we don’t recommend clicking them. It is always safer to check for updates using system tools. Then, a new spreading method was implied. From some time ago the cybercriminals use Remote Desktop Protocol (RDP) in order to get into computers. In other words, now the malware looks for the vulnerable RDP channels on the Internet and connects to them. After having the access, the scammers can install Crysis ransomware on all devices of this network.
Symptoms of Crysis Ransomware infection
It’s difficult not to notice ransomware, since it often has one of the processes responsible for displaying a notification message. This window blocks the screen leaving the user minimum alternatives. Besides, some files will be inaccessible, as in many cases ransomware encrypts them to exasperate the scaring effect.
What to do if your PC is infected with Crysis Ransomware
As soon as you notice the presence of the ransomware on your system, you should turn your computer off. If it is possible try to create a backup or image of your hard drive info. This may let you to reserve the state of your drives in case a decryption method would be created afterwards.
How to remove Crysis Ransomware?
To make sure that the adware won’t reappear, you need to delete Crysis Ransomware completely. For this you need to remove the files and registry entries of the ransomware. We should warn you that performing some of the steps may require above-average skills, so if you don’t feel experienced enough, you may apply to automatic removal tool.
Performing an antimalware scan with Norton would automatically search out and delete all elements related to Crysis Ransomware. It is not only the easiest way to eliminate Crysis Ransomware, but also the safest and the most assuring one.
Steps of Crysis Ransomware manual removal
Restart Windows in Safe Mode
For Windows XP:
- Restart the system
- While computer is rebooting press F8 several times
- In the appeared list of options choose Safe Mode
For Windows 7 and Vista:
- Restart the system
- While computer is rebooting press F8 several times
- In the appeared list of options choose Safe Mode
For Windows 8 and 8.1:
- Restart the system
- While computer is rebooting press F8 several times
- In the appeared list of options choose Safe Mode
For Windows 10:
- In the Start menu click on the power button
- Hold Shift and choose Restart
- Choose Troubleshoot
- In the Advanced Options choose Startup Settings
- Click Restart
- Select Enter Safe Mode
Delete files and registry entries added by Crysis Ransomware
Now you will be able to reach the needed functions and files. For eliminating the ransomware activity, you need to find all of the following items and delete them.
Remove Crysis Ransomware files and folders:
%WINDIR%\Syswow64\Skanda.exe
%WINDIR%\System32\Skanda.exe
%SystemDrive%\Users\balcao\AppData\Roaming\Skanda (1).exe
%WINDIR%\System32\Payload33.exe
%SystemDrive%\Users\CONSULENTE\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Skanda 10.exe
%SystemDrive%\Users\anne\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Skanda 8.exe
%LOCALAPPDATA%\_Skanda.exe
%WINDIR%\System32\Skanda.exe
%SystemDrive%\Users\TEMP.3801LIMITED\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Skanda11.exe
How to decrypt and restore .crysis files
Use the decrypting tool
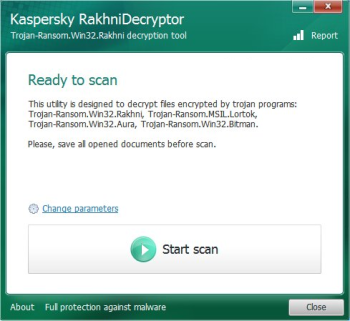
Kaspersky RakhniDecryptor is one of those tools that can be of an inestimable help in decrypting .crysis files. Since the tool requires no fee for using and had proved itself as an efficient utility, you definitely should try to decipher the files with it.
Restore .crysis files with an automatic tool
For those types of ransomware viruses that rather remove files than encrypt them we would suggest using Recuva program.
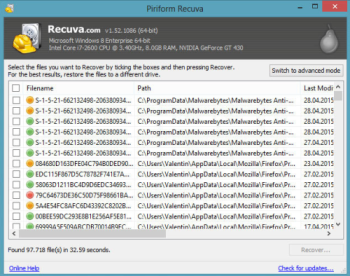
- Download Recuva tool and launch it
- Within the on-screen wizard choose the type of the files you want to recover
- Choose the location of the files
- Wait until the application finishes scanning
- Select the required files and click the Recover button
Nevertheless there are no other tools able to restore and decrypt .crysis files, you may try applying to the manual methods described below, however, they might not work with the latest versions of Crysis Ransomware.
Restore the system
- Initiate the search for system restore
- Click on the result
- Choose the date before the infection appearance
- Follow the on-screen instructions
Roll the files back to the previous version
- Right-click the file and choose Properties
- Open the Previous Version tab
- Select the latest version and click Copy
- Click Restore
If the above-mentioned methods didn’t help in eliminating the threat, then it’s better to rely on an automatic way of deleting Crysis Ransomware.
We also recommend to download and use Norton to scan the system after Crysis Ransomware removal to make sure that it is completely gone. The antimalware application will detect any vicious components left among system files and registry entries that can recover Crysis Ransomware.




