How to remove StorageCrypter Ransomware and decrypt .locked files
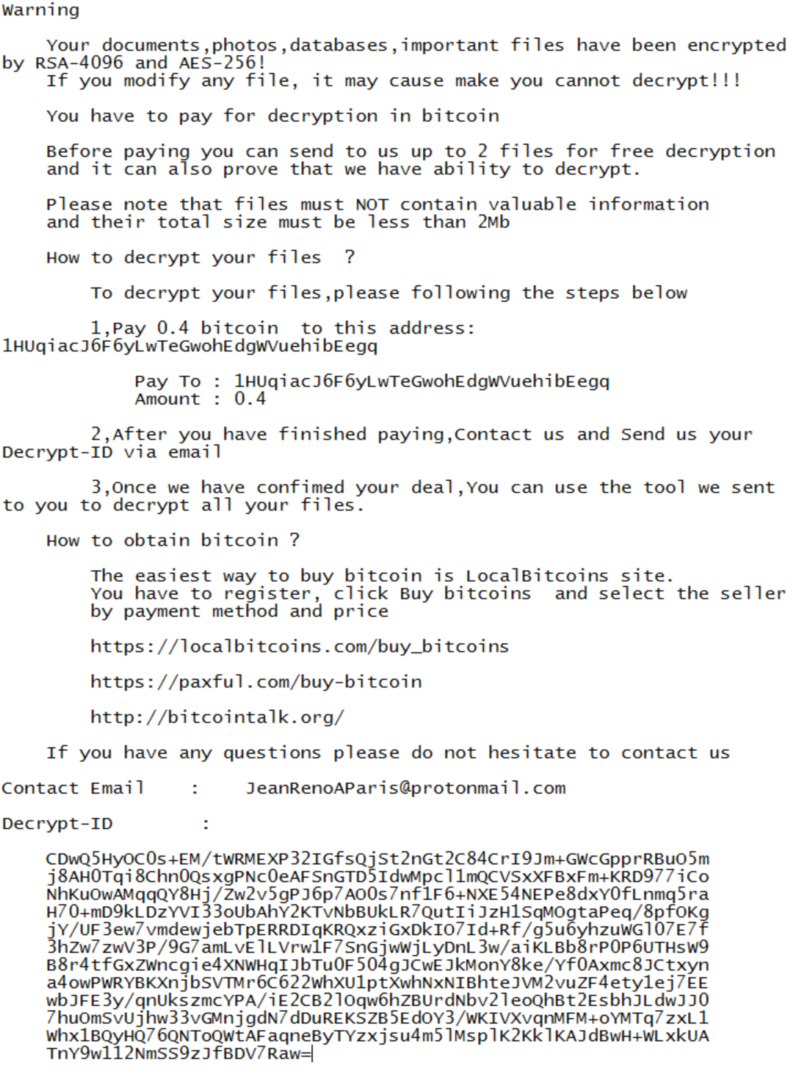
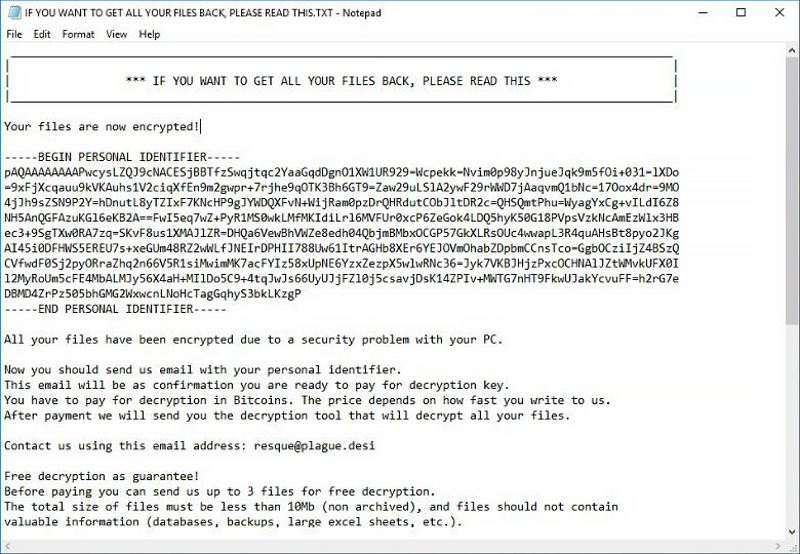
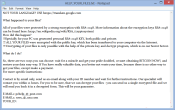
StorageCrypter ransomware is a dangerous encryption virus, especially for the different data on your PC, such as documents, photos etc. The virus encrypts all data files on your device. Besides that, it changes all filenames. Infected files have a [*.locked] extension and can't be decrypted manually. You can’t use infected files after encryption. All files with graphics become unreadable by graphics programs. Text documents look like random symbols. Also, StorageCrypter ransomware contains in all directories a file with name <_READ_ME_FOR_DECRYPT.txt>.