How to remove Search.searchmwpro.com

What is Search.searchmwpro.com?
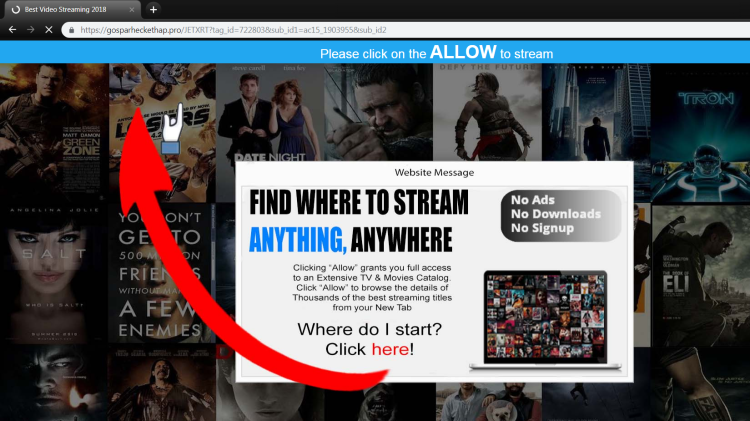
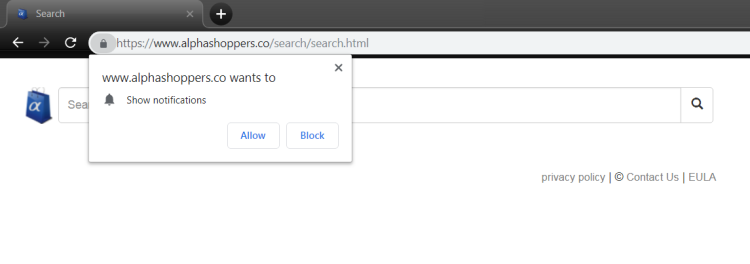
Search.searchmwpro.com is a misleading search site created for link promotion and advertising purposes. To succeed in this intention, the developers made it look like an ordinary search engine, still, the page gives itself away with a number of ads seen on it. Despite the fact that the page is intended to be a search engine, you shouldn’t use it for this purpose – bear in mind that the page belongs to malware and is used as a tool for misleading the users. When a search performed, the results are always unpredictable as the hijacker tends to replace the relevant pages with those that it promotes. To remove Search.searchmwpro.com and all its leftovers, you may seek assistance from the anti-malware program, it’s the most convenient way. Experienced users may use the manual way. Both methods are provided below.