How to remove CryptON Ransomware and recover ._crypt files
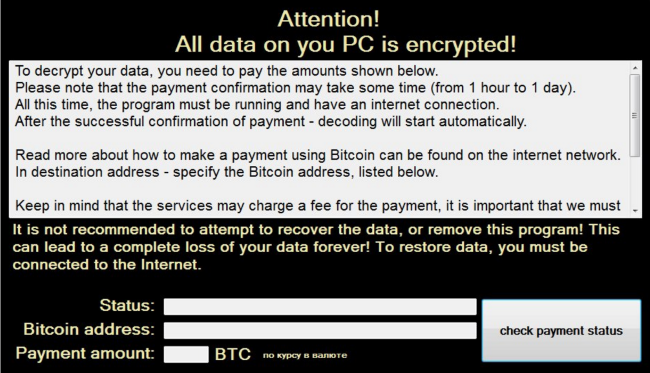
What is CryptON Ransomware?
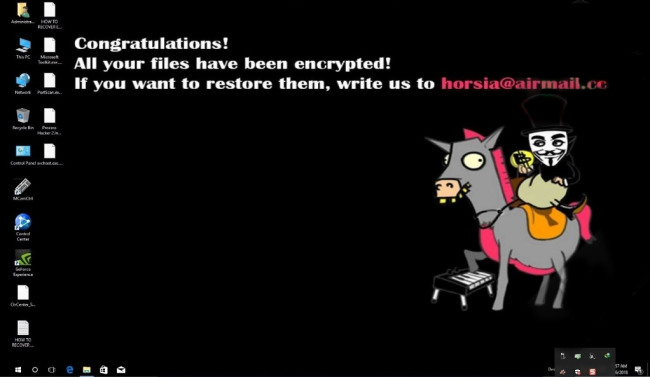
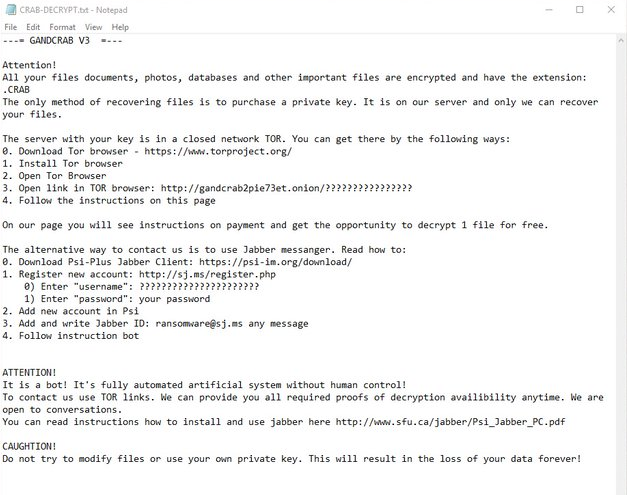
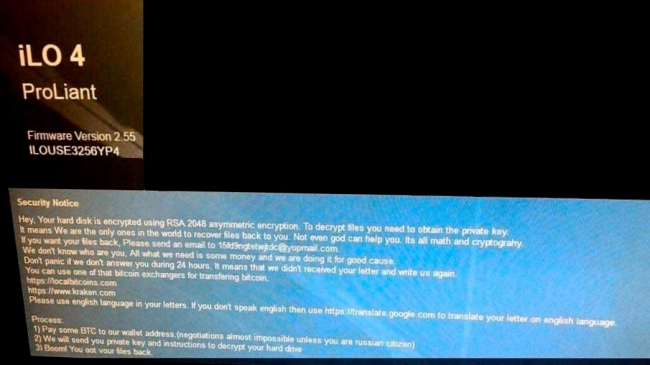
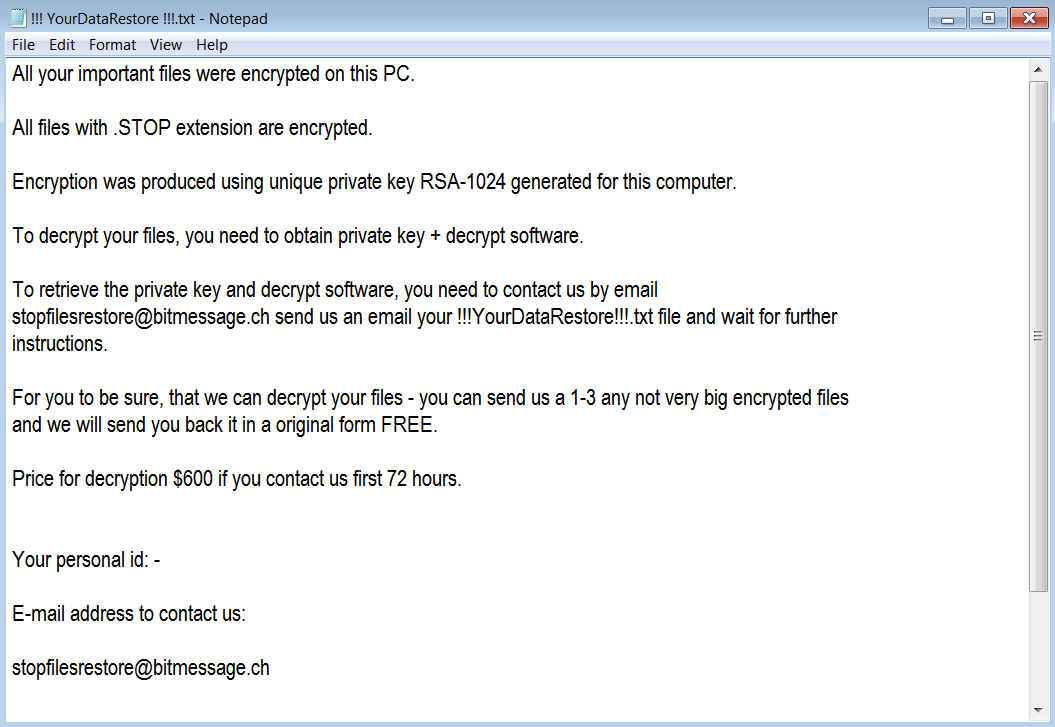
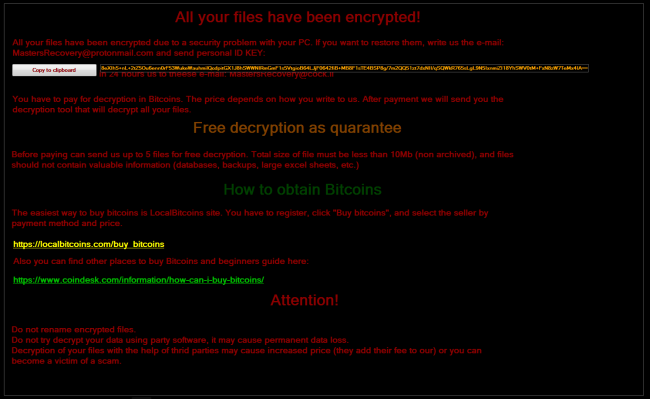
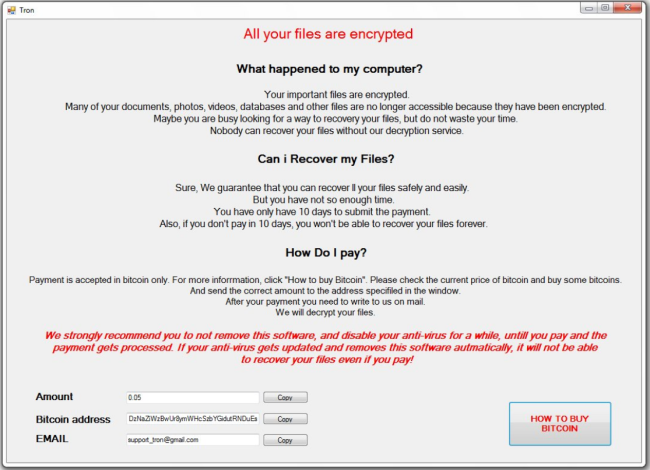
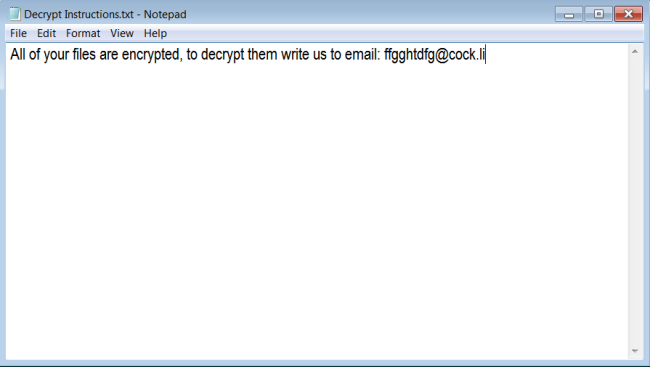
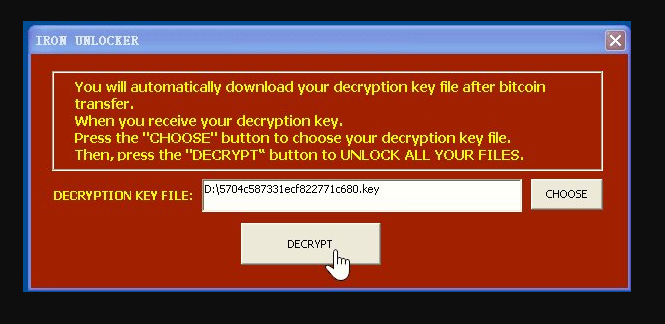
CryptON is an infamous virus that extorts money from users in exchange for their personal data. The point is, immediately after penetration, it starts to encrypt all sensitive files on victim’s computer using AES-256 complicated algorythm. In the process of encryption, all files get ._crypt extension, for example, file “mydoc.doc” will turn into “mydoc.doc._crypt files”. We also want to note that in some cases the extension might be different. At the time of writing the article, there are known following cases:
.id-_locked.id-_locked_by_krec.id-_locked_by_perfect.id-_x3m.id-_r9oj.id-_garryweber@protonmail.ch.id-_steaveiwalker@india.com_.id-_julia.crown@india.com_.id-_tom.cruz@india.com_.id-_CarlosBoltehero@india.com_.id-_maria.lopez1@india.com_