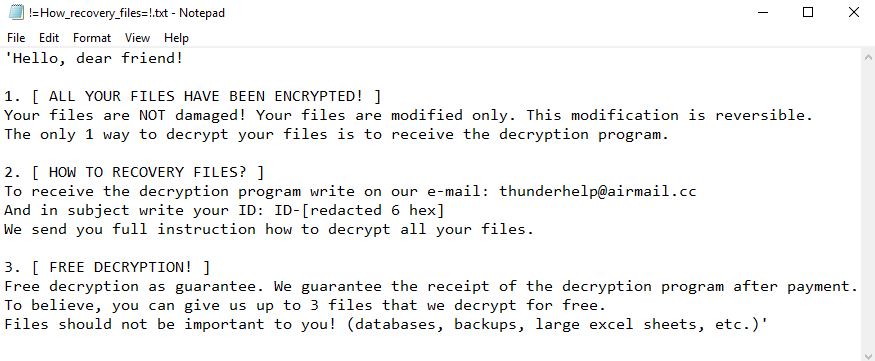
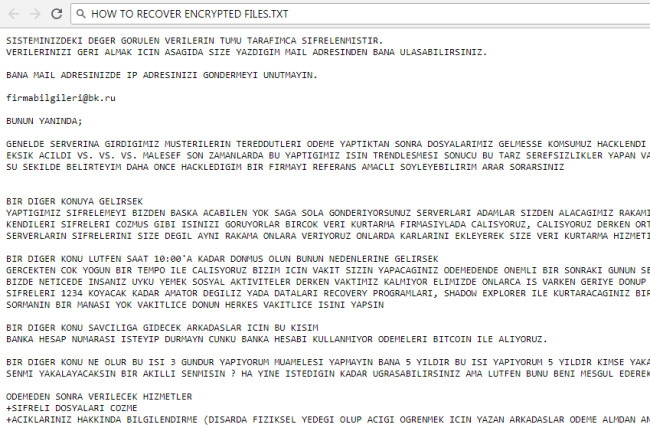
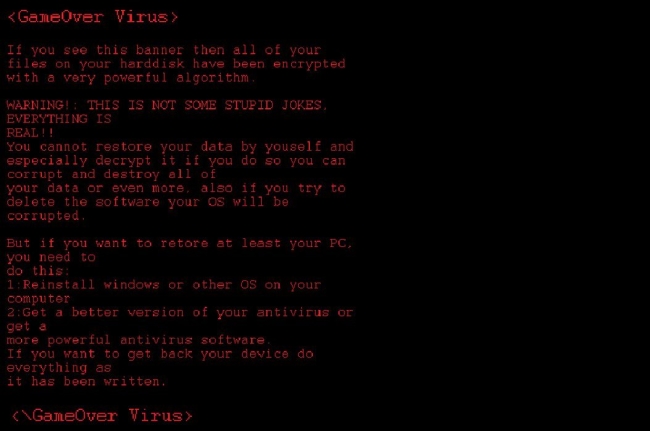
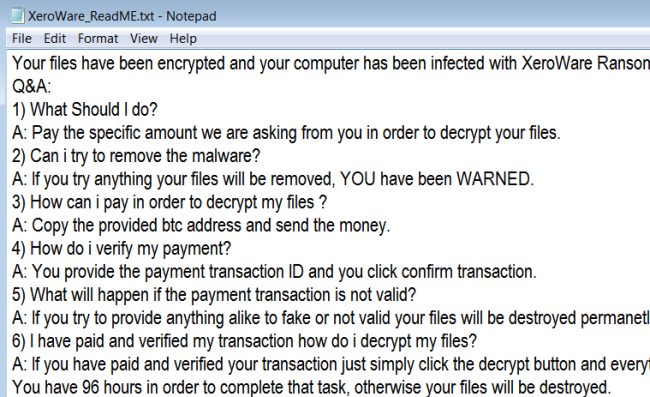
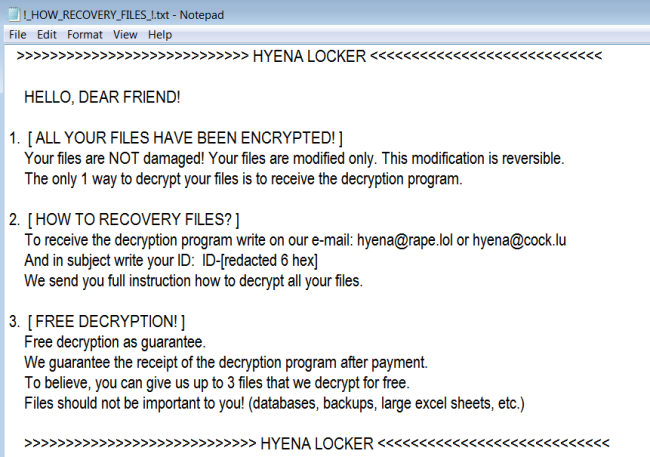
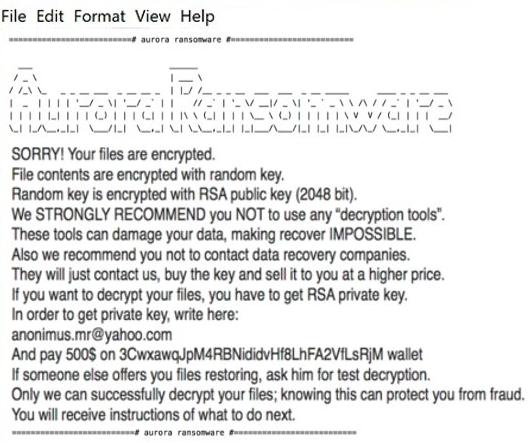
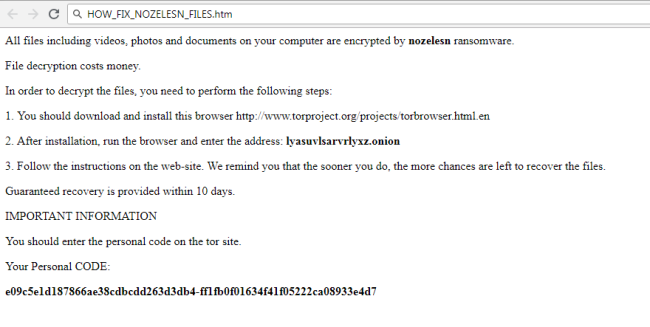
How to remove LockCrypt Ransomware and decrypt .lock files
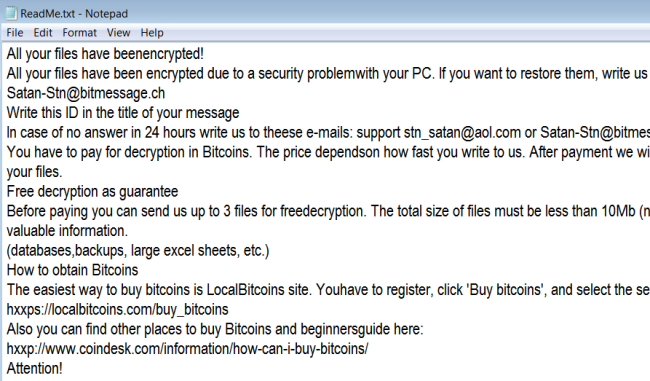
LockCrypt Ransomware is a data kidnapping virus which encrypts user data and asks for payment in exchange for the decryption key. The main distribution method of this virus is deceptive spam emails and shady websites containing malicious scripts. Once it gains access to the system, LockCrypt urgently launches encryption process in stealth mode, the culmination of which will be the loss of data.