How to remove Pepe ransomware
What Is Pepe ransomware?
Pepe is a computer pest will sneak into any type of device and begin to scan the system to find important files and block them with a special infectious algorithm
All files encrypted by the virus have the extension “.pepe” at the end of the familiar name. After encryption, a note from Pepe ransomware developers appears on the desktop screen:
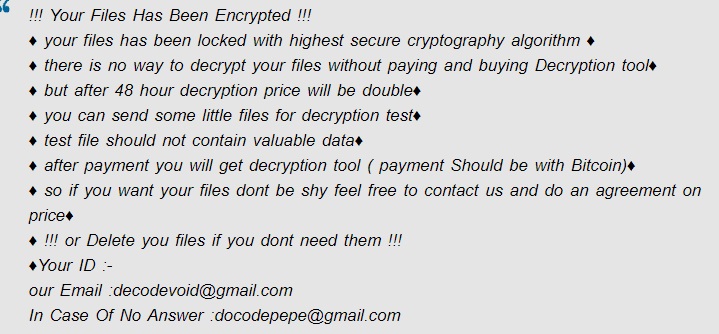
!!! Your Files Has Been Encrypted !!!
♦ your files has been locked with highest secure cryptography algorithm ♦
♦ there is no way to decrypt your files without paying and buying Decryption tool♦
♦ but after 48 hour decryption price will be double♦
♦ you can send some little files for decryption test♦
♦ test file should not contain valuable data♦
♦ after payment you will get decryption tool ( payment Should be with Bitcoin)♦
♦ so if you want your files dont be shy feel free to contact us and do an agreement on price♦
♦ !!! or Delete you files if you dont need them !!!
♦Your ID :-
our Email :decodevoid@gmail.com
In Case Of No Answer :docodepepe@gmail.com