How to remove Unblockupc ransomware and decrypt the files

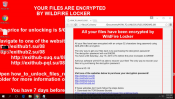
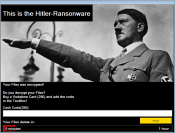
In the forefront of ransomware development, yet another hazard has appeared. Its name is UnblockUPC and it successfully utilizes the techniques that its predecessors use. It stealthily enters the systems and start encryption, after which the ransomware displays a notification with demands for decryption. The instructions for obtaining the decryption key are contained within Unblock your files.html, which states that the victim is punished for visiting illegal sites.