How to remove Aesir ransomware and decrypt .aesir files
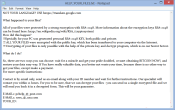
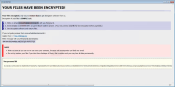
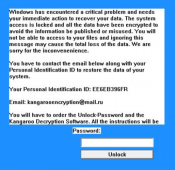
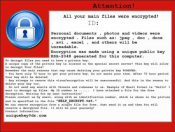
Aesir ransomware is a new release of Locky encryption virus. Mostly it has minor changes, as in the basic behavior it is identical to Odin, Thor, and Locky threats. So, in method of operation this malware resembles any other ransomware: it infiltrates the system stealthily and then searches for the files of the most frequent extensions. The scanned data afterwards becomes encrypted with asymmetric cryptography and the files get the .aesir extension.